Posts with tag "360 Secure Fabric"
Why Small and Midsize Businesses Need Modern Switches with Strong Security
Businesses of all sizes can improve security in an affordable way with modern switches.
Federal IT: Do You Know What’s Connected to Your Wired Networks?
When rogue devices join the network, they open the door to threats that can survive in the network for 100 days. That’s much too long.
Security is the New Standard
Designing and deploying networks with 360-degree security visibility is not an option. It is a must.
IoT Widens the Security Gap. Now What?
Ponemon Institute research explores the challenges of IoT security.
Put Access Control in Context with ClearPass and CarbonBlack
Strengthen your security defenses by considering the endpoint context in access control decisions.
Demonstrating Aruba 360 Secure Fabric at Gitex 2018: How We Did It
Showing partners and customers at Gitex how Aruba protects against insider threat.
Aruba Better-Together Security Approach Garners Industry Accolades
As AI-powered attack detection is now being integrated with both network access control and attack response, we are seeing the emergence of “next generation NAC”—providing 360 degrees of total attack...
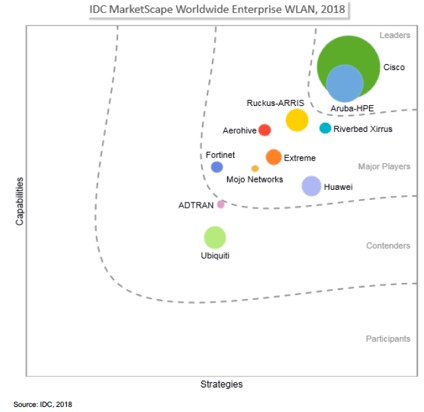
IDC MarketScape Report Ranks Aruba, a Hewlett Packard Enterprise company, a...
IDC recommends considering Aruba when wireless security and performance are paramount.
5 Risky Behaviors Your Employees Engage in Every Day
Even the best-intended workers can open the enterprise network to interlopers, while some legitimate users may exploit their authorized access to execute malicious activities.