Posts with tag "Authentication"
Crafting a secure, automated future for computer vision in manufacturing
Automate the onboarding of IIoT devices and mitigate risk with a new secure device identity solution from HPE Aruba and Axis Communications.
Guarding manufacturing operations with threat detection
IT/OT convergence has unlocked opportunities (and risks).
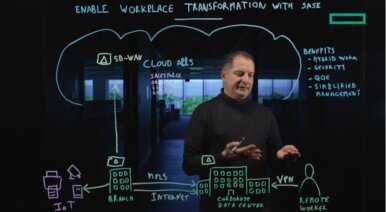
Top four benefits of SASE for the modern workplace
Explore the top four benefits of SASE that can enhance the modern workplace.
Cutting Through the Mist: Why Cloud-Native Doesn’t Mean Cloud-Only
Edge-to-cloud networking means that business solutions are now built, deployed and delivered at any point in your IT architecture—from the home or factory floor, to the data center to the cloud.
Passpoint: The Architecture
A look at how Passpoint works and ways to tie in enterprise wireless networks.
What is Passpoint?
What do the terms hotspot, hotspot 2.0, and cellular offload mean and what can they do for users?
Be Involved and Protect Your K-12 School
There are many traditional “things” found in schools that are making their way onto our wireless networks. Can you trust them?
Gaining Altitude with Python and APIs
Let’s take your previously learned Python skills and move them into production to automate deployment of a new WLAN.
Cybersecurity in a Zero Trust Architecture
Your traditional enterprise network security model may need to lose some trust.
A Zero-Trust Approach Helps Higher Education Close the Security Gap
Four ways to take action on cybersecurity, the #1 IT priority, across universities and colleges.