
The convergence of operational technology (OT) and information technology (IT) has ushered in a new era of efficiency and productivity in the manufacturing sector. However, this amalgamation also brings forth unprecedented security challenges. OT environment runs on legacy assets and architectures, rendering vulnerable due to inadequate or nonexistent security measures. That is why OT network penetrations and data breaches abound in every industry – energy generation and distribution, manufacturing, oil and gas, and others.
The reason is simple. OT devices have been designed with process reliability and application-specific architectures in mind. The primary objective is to make products that will work reliably for as long as possible. Cybersecurity expertise typically resides with the IT team. Until OT security can be asserted from the devices that generate the data to the applications that consume them, neither the devices nor the data can possibly be trusted.
Addressing these security shortcomings is not a trivial task. For the brownfield, the array of devices is vast, and finding secure replacements may not be either technically or economically viable. On the other hand, newer assets might possess the necessary capabilities to support the latest security mechanisms; however, the expertise to implement them is often lacking or sacrificed in favor of time-to-market or cost considerations.
HPE Aruba Networking presents a solution aimed at building trust where it is currently absent by simplifying the installation and integration of new OT devices, and enveloping legacy OT devices within security layers if they cannot be replaced. The objective is to transform untrusted devices into trusted data sources.
Detecting potential OT threats and adapting the network timely
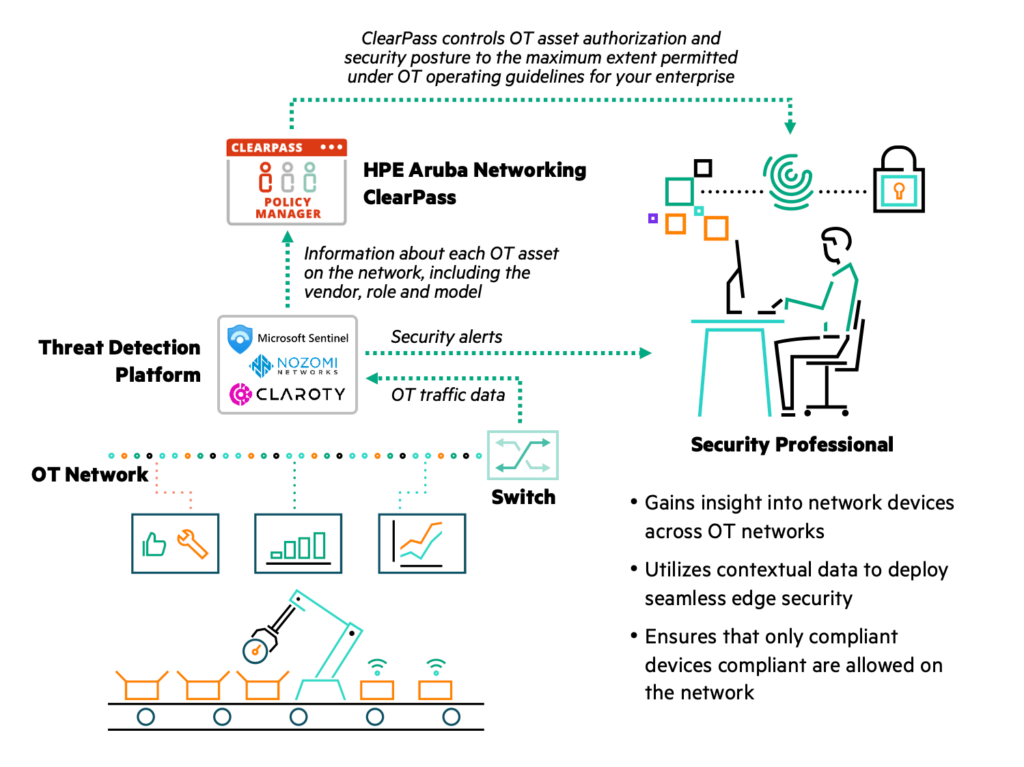
Aruba has partnered with OT security leaders like Claroty, Nozomi Networks and Microsoft, which make specialized systems to monitor industrial control protocols and devices. These advanced OT security systems couple deep knowledge of industrial control systems and machine learning-based threat analytics with a bi-directional link to ClearPass Policy Manager.
ClearPass Policy Manager uses device profiling, role-based access control, and real-time policy enforcement to identify, on-board, and control devices. The partner OT security systems enhance ClearPass’ capabilities by discovering industrial devices, flagging risks and abnormalities, and enforcing security postures. They can detect abnormal or unauthorized communication activity and equipment reconfiguration, and exchange security policy and device status with Aruba’s ClearPass Policy Manager for remediation.
For instance, when an IIoT device connects to the network it is discovered by the OT security system, which synchronizes with ClearPass Policy Manager to give it a comprehensive view of all IT and OT devices. The supplied context can be used to dynamically segment OT communications – a foundational element of a zero-trust framework – ensuring that devices only communicate with appropriate applications. ClearPass policies can control OT asset authorization and security posture to the maximum extent permitted under OT operating guidelines, up to and including device quarantines.
Benefits beyond threat detection
This solution offers many benefits for the security professional:
- Faster Incident Response: Take advantage of OT device status, attributes, and network communications.
- Compliance: Remediate systems with outdated or non-compliant software.
- Agility: Automatically enforce access policies for existing and new devices.
- Unified Platform: Manage network access in both IT and OT with ClearPass Policy Manager.
- OT Asset Inventory: Visibility into OT devices in your network.
- Vulnerability: Information about existing vulnerabilities in OT assets, including CVE score.
- Forensics: Asset information and network status for aftermath analysis.
The monetary impact of cyber incidents in OT environments cannot be underestimated. Downtime caused by cyberattacks can cost millions of dollars per hour. Additionally, the expenses associated with repairs, investigations, regulatory fines, legal settlements, and reputational damage can have devastating effects on a company's bottom line.
The marriage of operational efficiency and cybersecurity in manufacturing OT environments is no longer an option but a necessity. For more information, please visit Aruba Manufacturing Solutions.




