
Onboarding and managing cameras can be a daunting task
Cameras have quickly become an important data source for AI models in manufacturing and are used for task inspection, advanced process control, quality control, predictive maintenance (thermometric cameras), among other applications. An industrial network could have dozens, or even hundreds, of Ethernet-connected cameras on equipment, robots, along assembly lines, and facilities. Authenticating TCP/IP Ethernet-based cameras onto networks, managing certificates, configuring access, setting up VLANs and everything in-between during plant changeovers require skilled IT engineers. Onboarding, configuring, and managing so many devices throughout the lifecycle of a site can be costly and resource-intensive and, if done wrong, may lead to unplanned downtime.
A shortage of IT personnel has focused attention on opportunities to automate tasks like onboarding cameras and other IIoT devices onto secure corporate networks. IT has also hastened the transition from manually driven process to automated secure onboarding of IIoT devices based on four pillars: IIoT device recognition, secure authentication and onboarding, role-based access control and Zero Trust secure tunneling.
Automating the process and mitigating security risks
To address the automated IIoT device challenge, HPE Aruba Networking worked with Axis Communications, a division of Canon and world leader in IP-based cameras, to implement the IEEE 802.1AR secure device identity standard. 802.1AR uses Secure Device Identifiers (DevIDs) as device authentication credentials with Extensible Authentication Protocol (EAP) and other standards-based authentication and provisioning protocols.
As part of Axis Edge Vault, a device-centric hardware cybersecurity platform, Axis devices implement DevID services (called Axis device ID) by loading unique Initial Device Identifiers (IDevIDs) into a tamper-protected hardware cryptographic computing module at the time of manufacture. IDevIDs cannot be forged or transferred, and Axis Edge Vault protects the IDevIDs against probing. IDevIDs are supplemented with product-specific information, such as the common name and serial number, enabling Axis devices to inform the network about their available capabilities.
To simplify network authentication, Axis devices have enabled IEEE 802.1X port-based network access control by default and have the Axis device ID preconfigured. In joint deployments, the HPE Aruba Networking switch acts as the authenticator, allowing or blocking access to the network based on HPE Aruba ClearPass Policy Manager validation of the camera’s identity and digital certificates. Since IDevIDs and credentials are securely loaded into Axis devices at the time of manufacture, the entire authentication process is automated. Once ClearPass Policy Manager grants access, the policies assigned to the Axis device determine what network resources can/cannot be used. Other security infrastructure, such as next-generation firewalls, are notified by ClearPass Policy Manager when a new Axis device is onboarded at the network edge and which policies apply. If a firewall detects a policy violation, such as an attempt to reach a control node on the Internet, ClearPass Policy Manager will be notified and can quarantine the device.
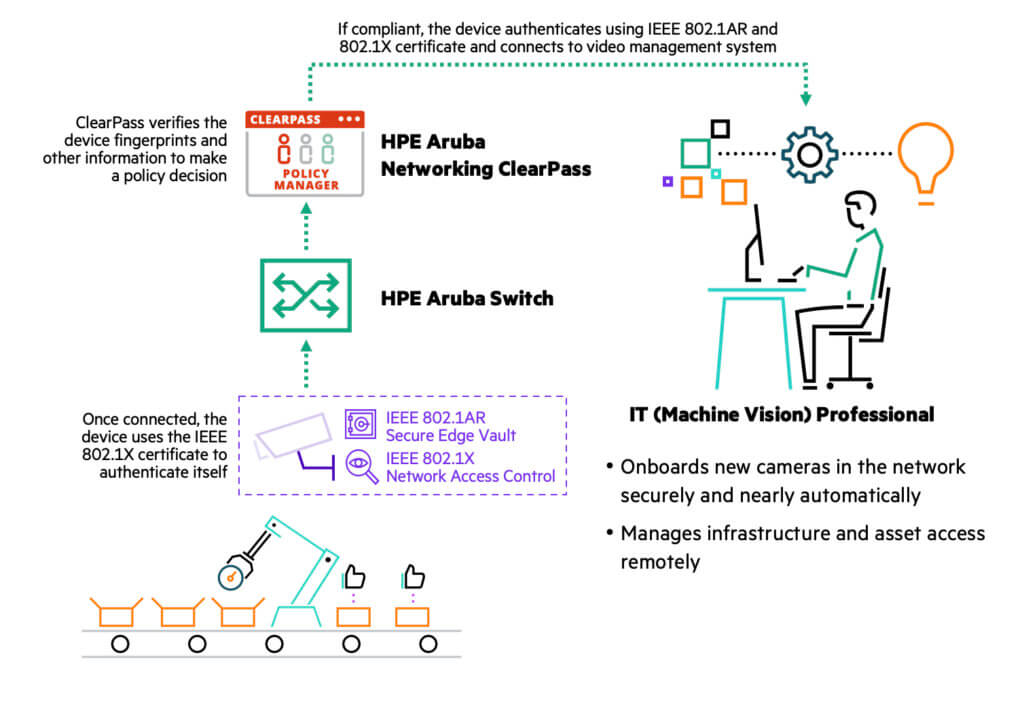
With the Axis device identified, authenticated, and onboarded, the system next establishes a dynamically segmented secure tunnel from the Axis device to its target application. HPE Aruba Networking’s Zero Trust framework ensures that authorized devices operate in their assigned swim lanes by using dynamic segmentation to establish least privilege access. It does this by segmenting traffic based on identity and associated access permissions, in this case allowing Axis devices to communicate only with their respective video analytics or card access application destinations consistent with their role.
Once the zero-trust tunnels are established, the four-step process is complete. Axis devices can securely communicate with their target applications, and all other traffic remains isolated and secure.
Benefits not necessarily limited to cameras
The solution reduces labor costs, speeds deployments, and helps avoid security gaps that can almost inevitably occur during changes to a site. The same process used with Axis cameras can be applied to any other Ethernet-based IIoT device that supports IEEE 802.1AR and IEEE 802.1X.
Learn more about HPE Aruba Networking and Axis Communications partnership.




