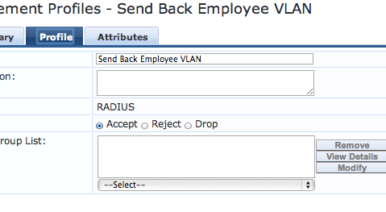
Authenticating users with Radius and Responding with a Pool (ArubOS 6.3 and above)
When you authenticate a user on an Aruba Controller with a radius server, you have the option of sending back an attribute that has either the role or the VLAN that a user will be in. The limitation...
Still Sweet on Suite B: NSA-approved Cryptography for Civilian and Military WLANs
NSA-approved Cryptography for Civilian and Military WLANs
How to Secure Mobile Devices for Government and Military Use
In spy movies, it always seems that government agencies are equipped with the most futuristic mobile gadgets imaginable. In the real world however, government lags behind the private sector in adoption...
Examining Different Approaches to BYOD
BYOD “Bring Your Own Device” has become a very popular industry term in the last couple of years. The core concept of BYOD is pretty simple and straightforward; allow users to use their own personal...
BYOD goes “Gangnam-Style” in 2013
Aruba recently participated in Vertical Systems Reseller (VSR) Annual Review and Outlook supplement. VSR do a great job with this piece, they describe it as & …
Watch Advanced “How-To” Videos on Configuring ClearPass
In under 5 minutes we'll show you how-to configure Policy Manager to use Microsoft Active Directory for EAP-PEAP authentication *and* we'll show you how-to configure. Radius Proxy on ClearPass Onboard...
Secure authentication with only a password
Cloud services are now being used to crack passwords used in WPA2-PSK. One researcher used the Amazon cloud to check over 400,000 passwords per second at a cost of less than a penny. He claims he can find...