In the earlier posts of this series, I delved into an overview of Passpoint, the Passpoint architecture and then deploying Passpoint. In this post, I will look at the data flow and how we actually access the carrier network through an Aruba wireless LAN.
Setting the Stage
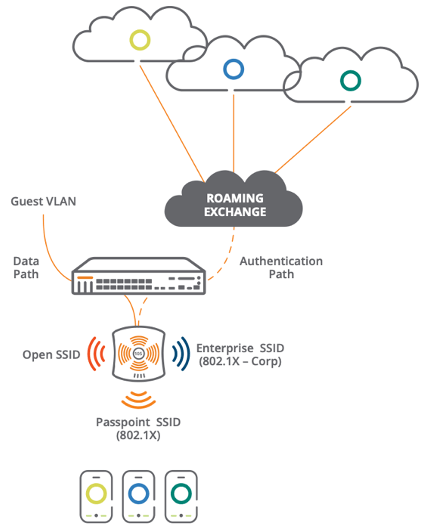
Going back to the architecture post for a minute so we can look at the setup again, a Passpoint SSID is being broadcast within the enterprise wireless network. This SSID then takes the normal data path through the wireless controller, but the authentication does not go to the enterprise network. Rather, it goes to a Roaming Exchange that brokers the connection back to the carrier networks for authentication using the supplied credentials on the user's SIM card or pre-programmed into the device. There can be even more complexity built in using other authentication and role-based access servers like Aruba ClearPass or other such systems. That will be a discussion for another time.
With the diagram we have the basic flow of data and kind of see the paths we are taking, but what actually occurs?
Following the Path
There are a number of good resources on the Aruba website for Passpoint. Some I reference here, but one of the best resources I found was Chuck Lukaszewski’s presentation from Mobility Field Day 4 in August 2019. It is definitely worth a watch.
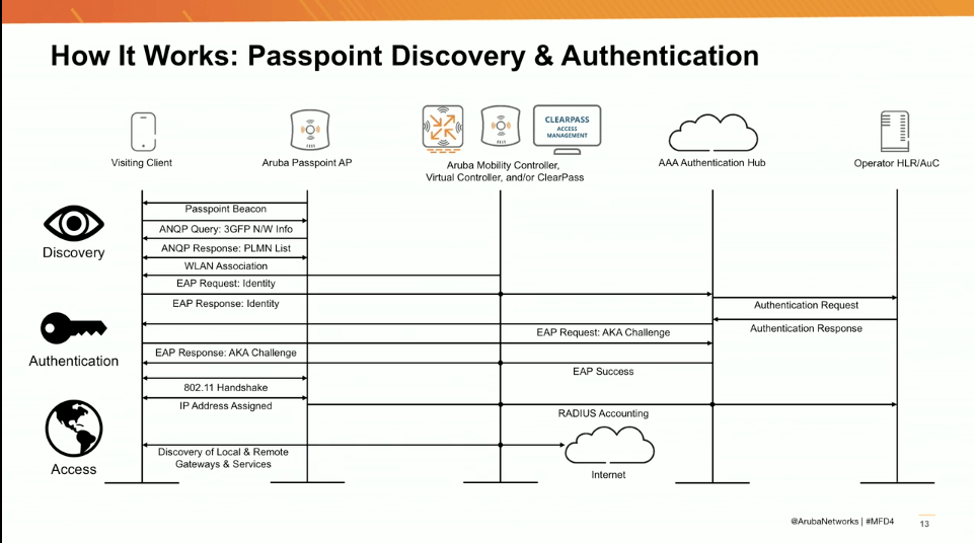
As the client comes onto the Passpoint network, it functions as a normal wireless device. However, there are added queries that happen that are not usually seen on a typical wireless client. During the discovery, a Passpoint beacon is sent out from the AP to the Passpoint-capable client. There is then an Access Network Query Protocol (ANQP) query, which allows devices to acquire pre-association information and parameters about the carrier networks being advertised with Passpoint. The initial ANQP Query returns the 3GPP Network Information.
What is the 3GPP? Glad you asked. There is a very detailed write-up on 3GPP from wi-fi.org, but we will just go at a high level. 3GPP is an element within the ANQP that holds the carrier network information which is tied back to the Public Land Mobile Network (PLNM). The information contained in the 3GPP is then added to the wireless profile for the network that will be supplying Passpoint connectivity. The device then compares the 3GPP with what is stored on the SIM card and determines if the carrier can be accessed through the Passpoint network. If the device’s carrier is found in the 3GPP, the device can then use the known EAP method for authentication, authenticates against the home carrier and then looks at the user and device policies to determine whether to continue using Passpoint or to switch to standard Wi-Fi for the connection.
That is a basic overview that takes us up through the 802.11 handshake on the above diagram. Looking at the diagram shows that there are two added steps to an otherwise standard 802.11 wireless association and authentication: Get the 3GPP info and check the PLMN ID. From there a usual 802.11 association begins until EAP identity is requested from the network. Since the device has knowledge of the carrier and has the credentials and connectivity information for that carrier, the EAP response goes back to the network, but is then forwarded through the wireless controller to the authentication hub/broker and then forwarded to the proper carrier. The carrier is then responding to EAP requests and challenges as opposed to the internal infrastructure.
Once EAP is cleared with the carrier, the usual 802.11 handshake takes place between the AP and client followed by the client receiving IP and network addresses. Then once again, the RADIUS accounting information is based through the enterprise network and sent to the carrier for accounting on itsnetwork. The Passpoint client then has full network connectivity to the Internet, messaging and Wi-Fi calling using carrier services delivered through the enterprise Wi-Fi network. Connectivity to internal resources from the Passpoint client depends on firewall, routing and possible role-based access controls.
Wrapping it Up
As my blog series has progressed, I have provided an introduction to Passpoint, an exploration the Passpoint architecture, how to deploy Passpoint, and finally the data flow in this post. From the outside perspective, Passpoint does not vary that much from standard enterprise wireless other than passing the data along to the carriers for authentication, accounting, and services.