
It’s Cybersecurity Awareness month, and you’ve no doubt seen a lot of references to Zero Trust and Zero Trust security models. With so much varied use, it can be difficult to understand exactly what it is and what it entails. Let’s look at some of the most asked questions about Zero Trust security models so you can separate the facts from fiction.
What is a Zero Trust security model?
“Zero Trust” has become somewhat of an industry buzzword lately, but it’s more than just a trendy term. Zero Trust security models refer to modern security paradigms that provide the least amount of access to network resources a user or device (referred to as a subject) needs to do its job, based on its role, and only if the subject is behaving appropriately.
One of the myths about Zero Trust is that it does away with the concept of trust altogether—that literally nothing is trusted. Instead, Zero Trust security models limit implicit trust based solely upon on how and where users are connecting. This is in contrast with a perimeter-based security model, in which subjects on a corporate laptop at a corporate office may be implicitly trusted to roam freely throughout the network. Malicious actors could exploit this broad access to expand their attacks and increase damage.
What’s an example of a Zero Trust security model?
One of the myths about Zero Trust security is that it is new or unproven. In fact, Zero Trust security models have existed for many years. If you’ve traveled by airplane within the last few decades, you’ve probably seen Zero Trust in action.
The National Institute of Standards and Technology, an authority on Zero Trust network architecture, popularized the notion of a Zero Trust security model functioning like an airport in which passengers, pilots, agents, visitors, and possibly some malicious actors mix. Within the terminal, access is limited because not much is known about these subjects—who they are or what their role is.
To gain greater access, subjects must pass through security screenings. Once they are identified and their purpose is established, they can be assigned a role that grants them access to more areas of the airport. For example, a pilot, passenger, and agent may be granted access to the boarding area, but only the passenger and pilot can enter the plane, and only the pilot can enter the cockpit. And if any of those individuals begins to exhibit behavior inconsistent with their role, as would a malicious actor seeking to access a restricted area, their access could be limited or revoked for further security evaluation.
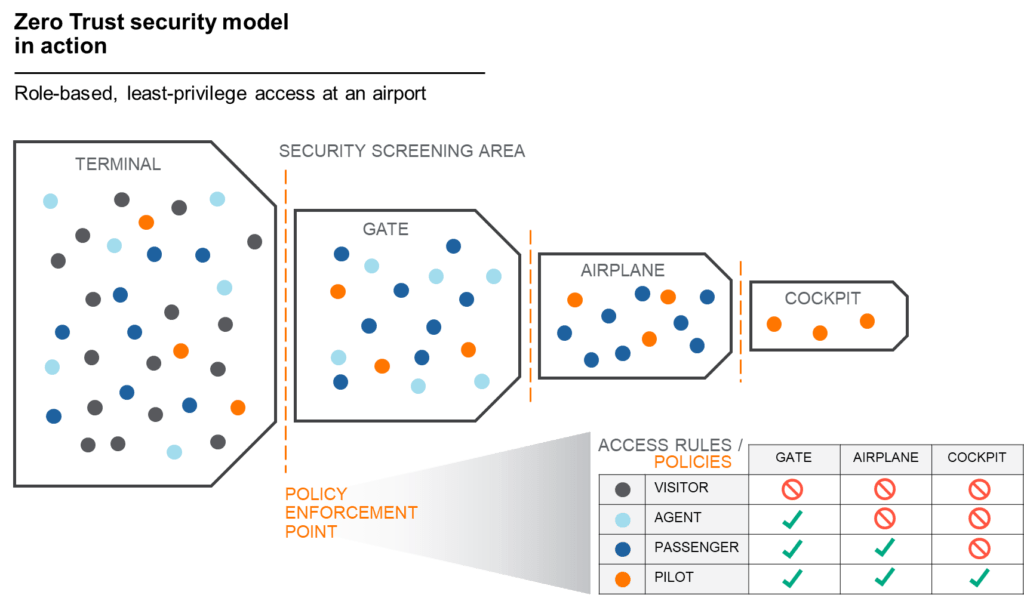
The sequential security screenings and restricted access protocols of a busy airport reflect a Zero Trust security model.
What are the benefits of a Zero Trust security model?
A common misconception about Zero Trust is that its drawbacks outweigh its benefits. What most organizations find is that Zero Trust security models offer significant benefits for not just network security, but also for meeting compliance mandates and improving operational efficiency. Zero Trust security models can help organizations by:
- Limiting access to resources—Unlike network security models that confer broad access to resources upon users, Zero Trust security models grants subjects the least amount of access to resources it needs to do its job. This practice not only limits the resources an attacker can access, it also limits employee and guest access to sensitive financial, patient, and customer data—critical requirements for PCI DSS, HIPAA, and GDPR.
- Detecting and preventing attacks—Attacks that exploit implicit trust, as when credentials are stolen or device addresses spoofed, may not be immediately detected by perimeter-based security strategies. In a Zero Trust security model, a subject’s behavior is continuously monitored against baselines, helping identify potential threats and trigger response.
- Reducing attack spread—The damage caused by an undetected cyberattack increases in an implicit-trust model when the attacker moves within the network. Zero Trust security models can reduce this lateral spread by automatically limiting or revoking access based on anomalous or suspicious behavior.
- Scaling with the organization—Within Zero Trust security models, least-privilege access is granted based on roles and policies, rather than a per-user, per-location, or per-device basis. That makes it easier for organizations to scale security as their number of users, devices, and locations increases, since roles and policies can be defined once and applied as often as needed.
What’s a simple Zero Trust security model checklist?
Have you heard that Zero Trust is not a single product that can be purchased off the shelf and implemented with the push of a button? Well, that is true. Many organizations find that adopting Zero Trust security models is a journey. Not sure where to start? Here is a checklist of capabilities to help you prioritize your next steps:
- Do you have visibility into every device on your network, even if you do not manage it?
- Do you have consistent methods for assigning privileges to users and devices?
- Are you enforcing standards of security compliance before a device is allowed on the network?
- Are you enforcing role-based access security policies consistently everywhere throughout the network?
- Are you able to continuously monitor a subject’s security state using all available data?
Ready to learn more about Zero Trust security models?
These resources can help you learn more about Zero Trust security models and how Aruba can help you support those strategies:
- What is Zero Trust?
- Building a Zero Trust security model with Aruba
- Aruba Zero Trust security solutions
You can also read other blogs in this month’s Cybersecurity Awareness series:




