
It’s Cybersecurity Awareness Month, and the focus is on protecting individuals and organizations from cybercrime.
One way organizations are addressing cybersecurity challenges is by adopting Zero Trust network security. However, fully implementing Zero Trust network security strategies can pose a challenge. Zero Trust focuses on providing and continuously monitoring least-privilege access to resources based on role, yet role-based access controls are often fragmented across multiple platforms which are not integrated.
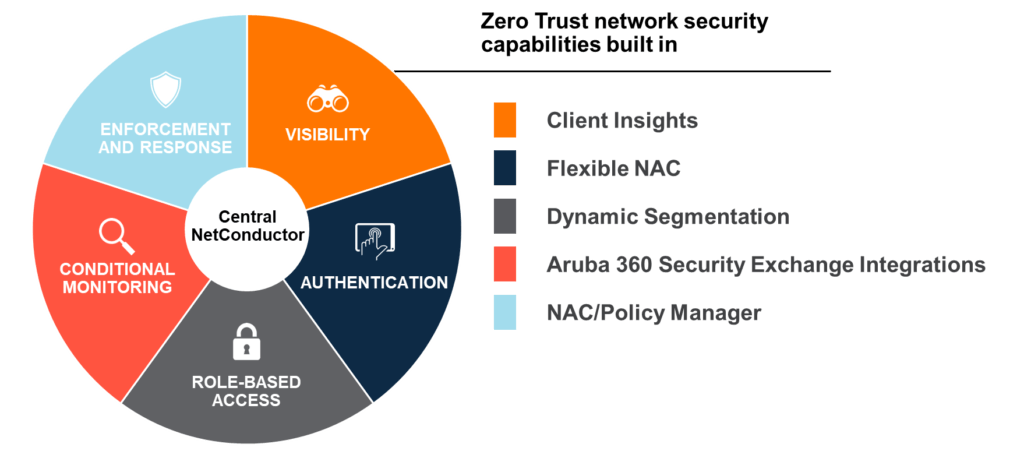
The five capabilities required for Zero Trust network security
Zero Trust network security frameworks are built upon five foundational capabilities:
- Visibility—identifying and profiling users and devices on the network
- Authentication and Authorization—defining roles and assigning granular role-based policies to users and devices
- Role-based Access—dynamically enforcing least-privilege access to resources throughout the network
- Conditional Monitoring—communicating real-time information bi-directionally within the security technology stack.
- Enforcement and Response—automatically responding to contextual threat signals by limiting or revoking access
Aruba makes it easier for organizations to adopt these capabilities with its Central NetConductor cloud-native network automation and orchestration solution. Part of Aruba Central, Central NetConductor includes all the tools organizations need to deploy, configure, and operate networks that support Zero Trust network security strategies.
With Central NetConductor, organizations benefit from built-in support for Zero Trust network security strategies.
Here’s how organizations can use Central NetConductor to begin their Zero Trust network security journeys.
Step 1: Understand traffic flows on your network
Zero Trust network security works by limiting users’ and devices’ access to resources based on their role and behavior. The first step is determining how endpoints map to roles and defining their least- access ruleset based on what the user/device needs to do on the network and what is considered normal behavior for that user/device.
Client Insights gives organizations a baseline of the types of data that different devices are sending. Telemetry data from Aruba infrastructure is sent to Aruba Central, providing not only visibility into traffic flows but also the ability to determine the types of endpoints on the network. Using tools like machine learning, Client Insights can easily organize and sort different device types into categories, like printers, cameras, and HVAC systems.
Step 2: Authenticate devices on the network
After identification, endpoints must be authenticated—ascertained with some level of confidence to be what they claim to be. A best practice is to authenticate each device first with the strongest method available, then to assess compliance with corporate endpoint policy before a role is assigned.
For example, employee laptops may first be authenticated using the 802.1X protocol, to determine with high confidence that the endpoint is indeed a laptop. The presence of corporate device management tools is confirmed, as well as the appropriate association between username, password, and device. Only after those checks are confirmed will the laptop be assigned an “employee” role.
Authenticating IoT devices can be a little more challenging. Organizations have traditionally relied on MAC-based authentication, but that may not yield a clear picture when IoT device vendors assign multiple device types to the same MAC address. Client Insights goes beyond MAC address and uses traffic flow to identify endpoints more accurately, so IT teams can assign roles to users and devices with greater assurance.
Step 3: Enforce trust
Aruba Central NetConductor gives organizations the flexibility to employ centralized and distributed models of trust enforcement. With Dynamic Segmentation, IT can consistently enforce the role-based access security rules applied to devices like printers anywhere in the network, providing true Zero Trust network security, where the only flows on the network are the flows that need to be on the network.
In addition, Central NetConductor makes it easier to adopt Zero Trust security models by reducing network complexity—no more VLAN and routing table spreadsheets, or manual configuration of ACLs required. At deployment, a fabric wizard simplifies the creation of overlays using an intuitive, graphical user interface, easing how virtual components are defined and configuration instructions generated and pushed to infrastructure. Post-deployment, access policies are automatically propagated throughout the network within minutes, so the network continually reflects the intended business workflows and associated role-based access without manual intervention or updating.
Watch Miles Davis demonstrate how Aruba Central NetConductor provides built-in support for Zero Trust network security frameworks.
Steps 4 and 5: Share context, respond to threats
Context sharing lets organizations use all the data available to them via the security ecosystem to make dynamic access decisions. For example, organizations can use Aruba’s market-leading network access control solution, ClearPass, with over 150 security partner tools (part of the Aruba 360 Security Exchange program) to ensure all the endpoints on the network have the desired security level. ClearPass can limit or revoke access for any device that does not meet security requirements or begins to behave inconsistently with its role.
An example of this in action: A security partner tool notices a printer is talking to a country on an excluded list or demonstrating some concerning IDS/IPS signatures. ClearPass receives that information and can then communicate to the network to move this device from a printer role to quarantine role, applying a different set of enforcement policies against that endpoint and ultimately ensuring there are no malicious devices not on the network.
Take the opportunity to learn more about Zero Trust network security and Central NetConductor with these resources:
- What is Zero Trust?
- Aruba Zero Trust security solutions
- Central NetConductor network and security automation and orchestration
- Videos: Streamline network and security operations with Central NetConductor
You can also read other blogs in this month’s series:




