
October is Cybersecurity Awareness Month. This month, individuals and organizations will refresh their focus on cybersecurity and, more importantly, cyber risk reduction. One way that organizations are combatting growing cybersecurity risk is with Zero Trust network security architectures.
Organizations are facing more cybersecurity challenges than ever
News headlines are dominated by cyber security incidents. Ransomware, phishing, denial of service attacks—it seems organizations are targeted with a never-ending array of cyberattacks. And those attacks are relentless. Recent reports suggest that weekly attacks on organizations have doubled since 2020.[1]
A successful attack can lead to a data breach: unauthorized access to and theft of valuable organizational information. What constitutes valuable information? Hackers are after all kinds of information these days: payment card information, patient health data, personally identifiable information, confidential strategic data, even incendiary email exchanges between executives.
Cyberattacks don’t just land organizations in the headlines—they also have economic consequences. In 2022, the cost of a security breach reached an all-time high: over $9M USD in the U.S., a 12% increase over last year’s costs.[2] It’s no wonder cyber risk reduction is top of mind for many organizations.
Traditional models of network security are no longer sufficient
Traditional perimeter-based network security approaches focus on where users connect from and the devices they use. Like gaining access to the inner areas within a fortress, a user on a campus corporate network, on a corporate device, is implicitly trusted with access to virtually any resource within the network perimeter.
This model has faced many challenges in recent years given rising IoT adoption, erosion of the corporate perimeter due to work-from-everywhere, and increasingly sophisticated threats that exploit “trusted” users and devices for malevolent purposes.
In addition, the broad access conferred upon implicitly trusted users makes it easier for attacks to propagate throughout the network, which is referred to as “lateral spread.” Lateral spread can lead to increased damage, more difficult remediation, and longer data breach response times.
Protecting the organization with Zero Trust network security
Instead of perimeter-based network security, organizations are now adopting Zero Trust network security strategies to secure their networks and protect their valuable resources.
Zero Trust security principles eschew the concept of implicit trust and instead require users and devices to prove their trustworthiness to gain access to just the resources they need for their role—what is necessary to do their job or fulfill their function. Trustworthiness is constantly re-evaluated, and if a user or device begins to act suspiciously or in a fashion inconsistent with their role, their access may be limited or revoked. This limited and dynamically assessed role-based access security can help minimize and even prevent lateral spread of attacks.
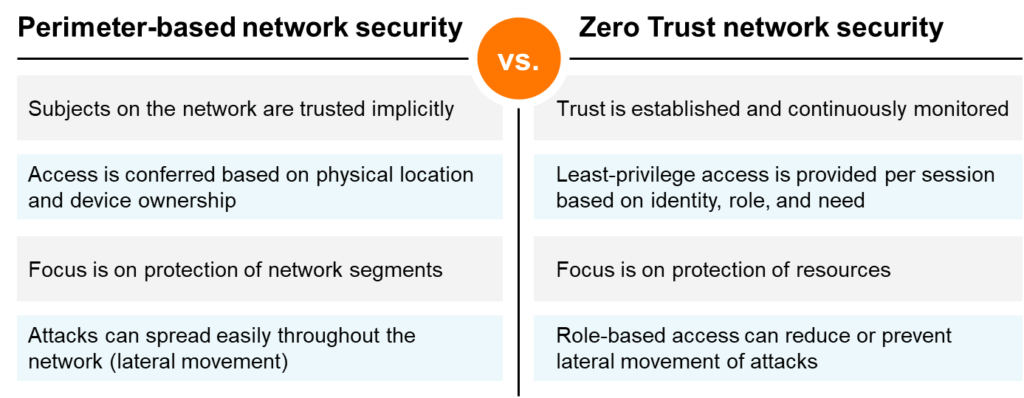
Zero Trust network security offers cybersecurity benefits vs. traditional perimeter-based network security models.
Five capabilities are needed to support a Zero Trust network security model
To support a Zero Trust network security model, networks must support five core capabilities.
- IT teams must be able to identity and profile the users and devices on their networks—even if they are not managed by IT.
- Authentication and Authorization. IT teams must be able to define roles and assign network access policies to users and devices with granularity.
- Role-based Access. Organizations must be able to dynamically enforce least-privilege access policies throughout the network.
- Conditional Monitoring. Elements within the security stack must communicate real-time telemetry information bi-directionally, to promptly identify behavioral anomalies and trigger action.
- Enforcement and Response. Based on contextual information received, IT must be able to automatically respond to threat signals to limit or revoke access and thus thwart potential attacks.
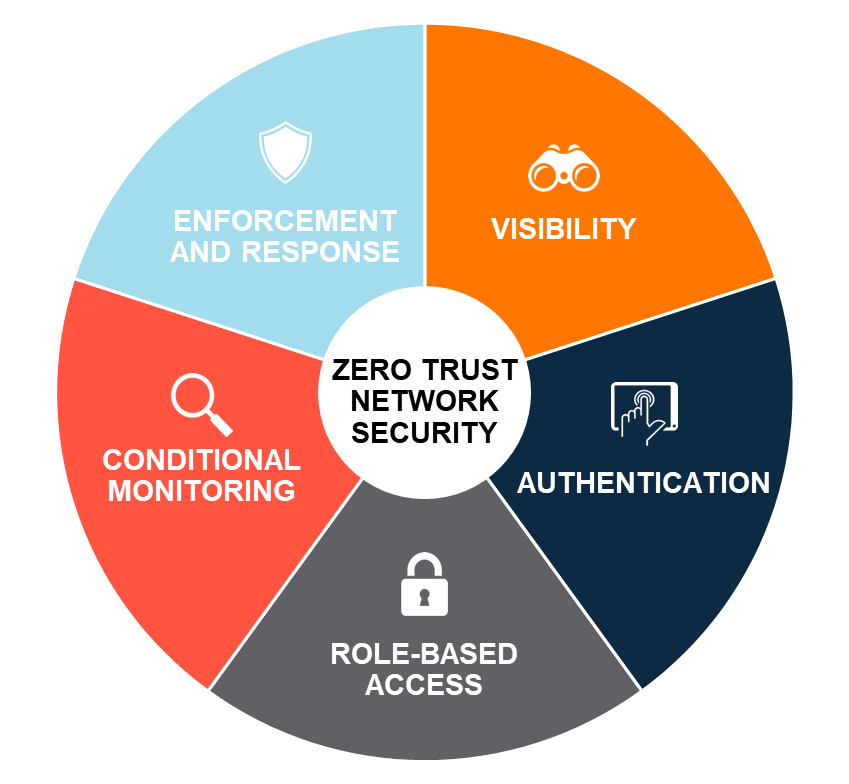
Five core capabilities—visibility, authentication and authorization, role-based access, conditional monitoring, and enforcement and response—form the foundation of Zero Trust network security.
How Aruba helps organizations implement Zero Trust network security
Zero Trust is a security paradigm—not a single product. For this reason, organizations may struggle to effectively implement the role-based network access controls at the core of Zero Trust network security. Aruba Edge-to-Cloud security solutions build in support for Zero Trust network security frameworks within Aruba Central, automating identity-based security controls and easing the adoption of Zero Trust security strategies.
Want to deepen your understanding of Zero Trust network security? Check out these resources:
- What is Zero Trust?
- Building a Zero Trust security model with Aruba
- Aruba Zero Trust security solutions
You can also read other blogs in this month’s Cybersecurity Awareness series:
- How to achieve 5 critical capabilities of Zero Trust network security
- Get the facts about the Zero Trust security model
-------
[1] Mims, C. “Hackers Know ... The Weakest Link Is You.” Wall Street Journal, Sept. 24, 2022.
[2] Ponemon Institute. Cost of Data Breach Report, 2022.




