
For decades, organizations have relied on a traditional architecture to secure their network based on firewalls and other perimeter defenses. As organizations massively moved their workloads to the cloud, users are now accessing sensitive data in the cloud through unsecured links, outside of the corporate network perimeter and from any device. This trend has accelerated as hybrid working has become the new normal.
Traditional architectures were centered around a perimeter-based security model, with the data center as the central hub for all network traffic. This architecture forced IT department to backhaul traffic to the data center for security reasons, significantly impacting cloud application performance. Traditional network architecture was also complex, with many devices and vendors to manage. It was prone to inconsistent security policies across branch offices as legacy devices had to be manually configured. Additionally, with hybrid working, IT departments are struggling to provide a secure access to remote employees and protect critical SaaS applications.
IT departments must now take steps to embrace SASE as traditional network architectures were never designed for the cloud.
SASE is the convergence of networking and security by combining SD-WAN with SSE (Security Service Edge) including ZTNA (Zero Trust Network Access), CASB (Cloud Access Security Broker), SWG (Secure Web Gateway) and FWaaS (Firewall as a Service).
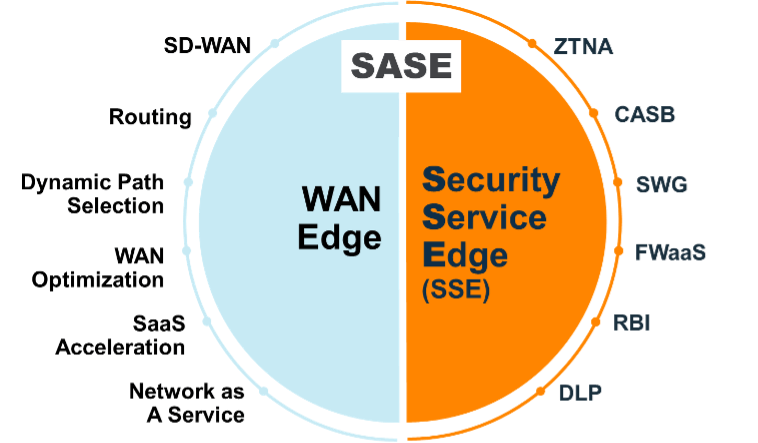
SASE combines SD-WAN capabilities with cloud-delivered security features (SSE).
Below are three use cases that organizations can explore to jump start their journey to SD-WAN, SSE and SASE.
1. WAN Modernization
Traditional architecture often uses MPLS links to connect branch offices to the headquarters. In this architecture, cloud traffic must be backhauled to the data center to perform security inspection, increasing latency, and therefore impacting application performance. Additionally, organizations lack flexibility. For example, they are unable to quickly deploy a new MPLS line and spin up a new branch.
SD-WAN is the foundational component of SASE. By virtualizing the WAN, it combines multiple links including MPLS, broadband internet and 5G. SD-WAN constantly monitors network conditions and quickly adapts. It gives the flexibility to use any type of links by mitigating the effects of jitter and packet loss with techniques such as Forward Error Correction (FEC).
With SD-WAN, data in transit are protected thanks to encrypted IPsec tunnels. SD-WAN also securely and intelligently steers traffic to the cloud over the most optimal path. Trusted applications such as Microsoft 365 or RingCentral are directly sent to the cloud while other applications are sent to cloud-delivered security solutions (Security Service Edge) or sent to the data center.
An advanced SD-WAN solution also includes other functionalities such as next-generation firewall, routing and WAN optimization capabilities. Configurations and policy definitions are centrally orchestrated and automatically pushed to branches through zero touch provisioning. This enables organizations to streamline network operations by replacing legacy equipment such as routers and firewalls. Thanks to its next-generation firewall capabilities, an advanced SD-WAN also helps secure IoT devices with fine-grained segmentation based on role and identity.
Implementing SD-WAN is the first step to SASE. It provides a secure and flexible way to connect remote users to cloud-based applications and services. It helps reduce capital and operational costs by simplifying WAN architecture, centralizing network and security management, and eliminating the backhaul of cloud-destined traffic across expensive leased line circuits. It also provides visibility and control over the network which is critical in a SASE architecture.
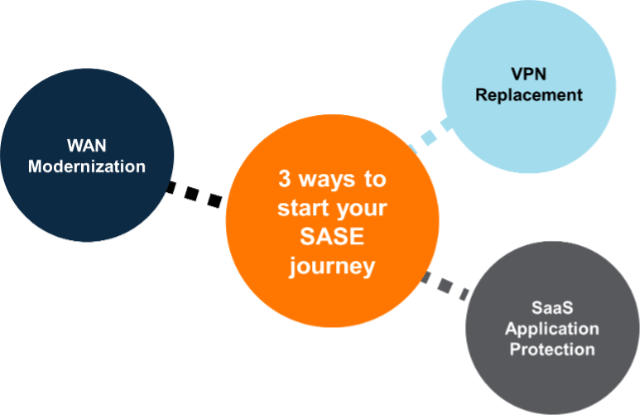
Three ways to jump start your SASE journey.
2. VPN Replacement
VPN (Virtual Private Network) is a technology that provides a secure, encrypted connection over the internet. When a remote worker connects to a VPN, a secure tunnel is established to the VPN server, making it virtually impossible to intercept or decrypt the data. Reciprocally, it enables employees to access corporate resources remotely from any location. It is also more cost-effective as it uses internet links instead of expensive private lines. VPN also helps comply with regulations that mandate the use of VPNs when dealing with sensitive data.
ZTNA (Zero Trust Network Access), part of SASE is based on the principle to “never trust, always verify”, so that a device connecting to the network is not trusted by default, even if it is connected from a corporate network. It enforces least-privilege access by ensuring users only access the resources they need to perform, based on their roles in the business, reducing the attack surface and the risk of data breaches.
ZTNA is often compared to VPN, but it offers several advantages over VPN.
One of the main drawbacks of VPN is that it gives unlimited access to the enterprise network once a user is identified, while ZTNA segments the network at the application level based on user identity. This provides a more granular access control to resources than traditional VPN. It is also more secure, as access is granted on a need-to-know basis, only after the user’s identity and device are verified. It is easier to manage as access policies are centrally managed and can be updated in real-time.
Once ZTNA has been implemented in the organization, IT departments can easily deploy other SASE functions such as SD-WAN to modernize the network or cloud-delivered security capabilities such as CASB (Cloud Access Security Broker) or SWG (Secure Web Gateway).
3. SaaS application protection
As more organizations adopt cloud services, it is key to ensure security and compliance of cloud-based data. More sensitive data travels over unsecured links and are hosted outside of the enterprise security perimeter in sanctioned or unsanctioned cloud services. With that in mind, organizations must detect potential data breaches and prevent them by monitoring and blocking unsafe movement of sensitive data.
Cloud Access Security Broker (CASB) monitors user activities in cloud services, identifies potential security risks and policy violations to prevent data loss. It identifies and detects sensitive data in cloud applications and enforces security policies such as authentication and Single Sign On (SSO). It prevents users from signing up for and using cloud applications that are not authorized by an organization’s IT and security policies, significantly reducing shadow IT.
To protect the organization against web-based threats such as malware, ransomware, phishing and other cyber security risks, a Secure Web Gateway solution (SWG) sits between a user and a website to intercept web traffic. It performs several security inspections including URL filtering, malicious code detection and web access control, and provides policies that can limit access to adult sites, gambling, or dangerous sites for example. It also provides real-time threat detection and response, allowing organizations to quickly respond to potential security incidents.
In summary, SWG and CASB ensure that users safely access the internet while gaining visibility and control over the use of cloud services. Depending on their business and security goals, organizations can continue their journey to SASE by deploying SD-WAN or ZTNA capabilities.
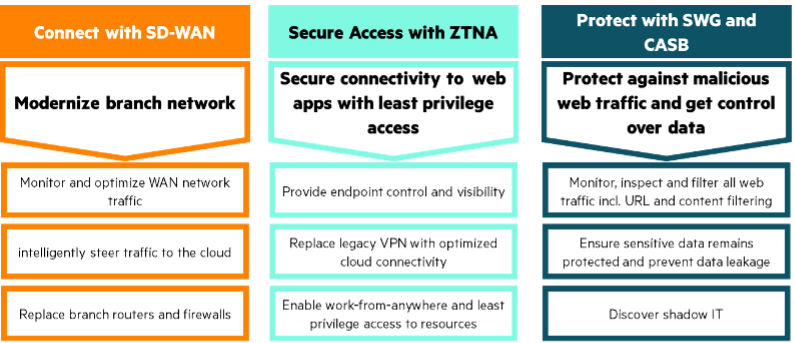
Three use cases to start your SASE implementation in your organization.
Aruba EdgeConnect is a secure SD-WAN solution that provides a solid foundation to build a robust SASE architecture. It supports cloud-first organizations by intelligently steering web traffic to the cloud and helps them simplify their WAN infrastructure by replacing legacy routers and next-generation firewalls through a single platform. The solution tightly integrates with multiple SSE vendors including Zscaler and Netskope providing unequalled third-party interoperability and freedom of choice.
To meet the demand for an integrated network and security solution, Hewlett Packard Enterprise recently announced the acquisition of Axis Security, expanding its edge-to-cloud security capabilities by offering a unified SASE solution. Axis Security offers a cloud-native SSE platform, Atmos, with zero-trust network access (ZTNA), secure web gateway (SWG), cloud access security broker (CASB), and digital experience monitoring (DEM) capabilities.
For more information about Axis Security acquisition, please consult our press release.
Other resources:
Aruba EdgeConnect SD-WAN web page
Architecting a secure business-driven SD-WAN




