
This is part 4 of a 4-part blog series. Read the series:
Part 1: Optimize CX switch performance using HPE Aruba Networking Central
Part 2: Configuring CX switches made easy using HPE Aruba Networking Central
Part 3: Real-time AI-powered CX switch insights with HPE Aruba Networking Central
If most of your network issues arise due to manual errors, then you are not alone. According to the latest report by EMA on network configuration management and automation, 50% of organizations find network configuration time-consuming due to reliance on CLI or scripts. Additionally, 9 out of 10 network issues are due to human error. As businesses shift to hybrid work models, they overhaul outdated processes to stay competitive, emphasizing efficient IT strategies. Managing network switch capabilities becomes pivotal for user experience, network security, and operational efficiency. However, deploying, configuring, and managing network devices located across enterprise, campus, and remote sites is complicated and resource intensive. But what if your network was automated and could comprehend your business intent for all your environments through a single dashboard?
If you have previously read the three blogs in the series “4 ways Central can simplify CX switch management,” you already know that HPE Aruba Networking Central offers unified management with simple and automated workflows for Day 0 thru Day N tasks to enable an efficient network. In this final blog of the series, you will learn how the synergy between CX switches and Central can help IT teams pivot towards better network security posture by defining and applying role-based policies based on business intent across campus, branch, and data center environments. Furthermore, teams can avoid using manual or scripted methods of VLAN, VRF, ACL configurations, reducing scope of any human error.
Telemetry from CX switches for network security and visibility
Companies can define and implement their business intent once they have complete visibility into the devices connected to the network. Client Insights (available with a Central Foundation license) leverages network telemetry from CX switches, APs, and gateways to determine the type of endpoints on the network and the type of traffic these devices are sending without requiring the installation and maintenance of physical collectors or agents. By enabling client IP tracker and device fingerprinting in the UI configuration menu, users can easily capture client telemetry for Client Insights. AI/ML models are then used to identify and profile the wired clients connected to these CX switches and group them into categories, like corporate laptops, printers, cameras, HVAC systems etc. Post profiling, access privileges can be applied using roles, and organizations can get a step closer to their Zero Trust Security requirements.
Enhancing network security with distributed policy enforcement in line done by CX switches and gateways
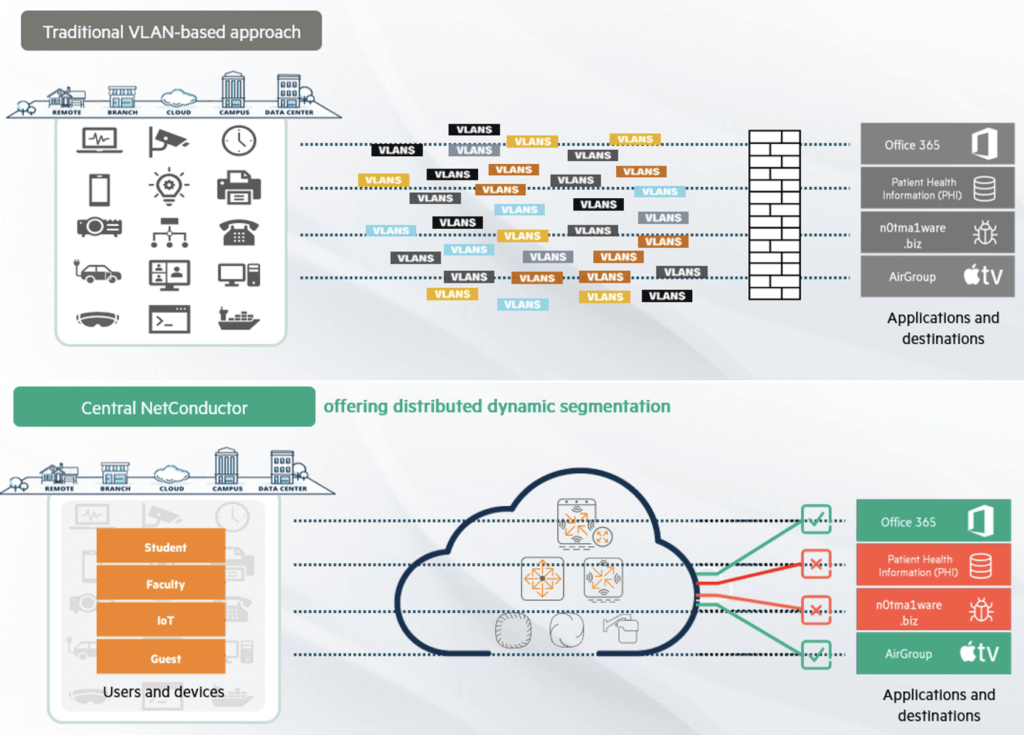
Gartner predicts that once intent-based networking is adopted, redundant and tedious configuration tasks by network admins can be eliminated. Central NetConductor, available with Central Advanced licenses, aids network and security teams to automatically configure LAN, WLAN, and WAN infrastructure and deliver optimal network performance while enforcing granular role-based network security policies that are essential to Zero Trust architectures. Organizations can adopt different models — centralized or distributed — to enforce these role-based policies across campus, branch, and data center environments.
In the latter method, IT operators can create intelligent overlays, or fabrics, for campus and data center environments through the fabric wizard (a service of NetConductor) using an intuitive, graphical user interface, easing how virtual components are defined and automatically generating configuration instructions that are pushed to CX switches and gateways. Client traffic and network security policies are decoupled from the underlying network construction—no more VLAN and routing table spreadsheets, or manual configuration of ACLs is required. Distributed fabric and role-based policy enforcement can be created for sites up to 1000 access layer switches, making it ideal for any deployment size. Multiple fabrics can also be created, and role propagation is achieved by the CX switches deployed at the border layer without the need for gateways. This enables policy enforcement between multiple fabrics across the entire network.
This form of distributed policy enforcement reduces network latency as traffic doesn’t need to be diverted to a separate security appliance, so there’s no compromise between network security, protection, performance, and user experience. Additionally, overlays significantly reduce network complexity and provide holistic control of the network, eliminating the need for labor-intensive management of physical and virtual infrastructure, or manual configuration of networks using VLANs or ACLs, helping organizations save time and money.
Network Insights provide health scores that can help IT teams monitor overlays, sites, and devices and troubleshoot network issues that may otherwise be difficult to pinpoint, such as route, tunnel, and segment status. Central NetConductor is designed for interoperability as it uses widely adopted protocols such as EVPN/VXLAN to produce the intelligent network overlays. As a result, Central NetConductor-capable infrastructure can coexist alongside current network management and network security services, protecting investments and enabling organizations to modernize networks at their own pace.
The network: A new driver of innovation and protection
Whether enabling hybrid work or advancing new business models, the network plays an increasingly critical role in driving the business forward. Whether via traditional on-premises connectivity or the Internet and the cloud, the network’s mission is to collect, secure, and deliver data and IT resources to users, devices, and applications wherever and whenever it’s needed. Given the ubiquitous nature of the network, it is only natural that it is now considered a bridge between connectivity and security.
With Central NetConductor, the network becomes a Zero Trust Security solution that can help teams achieve connectivity and security objectives. Part of the HPE Aruba Networking security-first, AI-powered networking portfolio, Central NetConductor provides a common Zero Trust foundation for networking and security teams to power distinctive experiences and innovative business results—without sacrificing cybersecurity protection.
Central NetConductor delivers advanced visibility, insights, centralized policy management, data protection, threat defense, and access control in a single platform. AI-powered networking helps teams benefit from intelligent automation that reduces manual effort, improves visibility and anomaly detection, and enhances monitoring and diagnostics, all of which ensure the organization is not exposed to unnecessary risk.
Improving network security, winning awards, and delivering customer benefits
Still not convinced about the benefits of NetConductor? CRN recently recognized NetConductor as a “2023 Product of the Year.”
In addition, the high degree of network automation achieved by Central and CX switches significantly reduces the amount of IT resources required for ongoing network configuration, lowers MTTR, and improves overall network security posture. Central has even helped increase customers' profits, as seen in this Homebase case study. Standing true to the “customer first, customer last” approach, HPE Aruba Networking ensures that we help our customers at every juncture and help them transition to a modern network.
Explore more about network security and Central NetConductor
Orchestrate and automate network and security services with Central NetConductor
How to achieve 5 critical capabilities of Zero Trust network security
Easing migration to role-based policies
Microsoft Office 365 is a trademark of the Microsoft group of companies. Apple TV is a trademark of Apple Inc., registered in the U.S. and other countries and regions.



