
As end users adopt software-defined technology that can help them more easily deploy and manage secure networks, they are increasingly looking to the technologies known as secure access service edge (SASE) and secure service edge (SSE).
But digging deeper into these acronyms, it gets more complex. SASE and SSE products aren’t exactly product categories per se – but platforms for integrating a variety of network security functions. These wide-ranging features might include all the most popular features/acronyms, including Advanced Threat Protection (ATP), Cloud Access Security Broker (CASB), Data Loss Prevention (DLP), Firewall-as-a-Service (FWaaS), Intrusion Detection System/Intrusion Prevention System (IDS/IPS), Next-Generation Firewall (NGFW), Software-Defined Wide-Area Networking (SD-WAN), Secure Web Gateway (SWG), Unified Threat Management (UTM), and Zero Trust Network Access (ZTNA). The integration of these functions is a key driving force behind the growth of the SASE market.
The creation of the SASE and SSE categories grew out of the software-defined networking market, which enabled software-based orchestration of network security functions. SD-WAN helped orchestrate and manage virtualized network connections, while SASE and SSE orchestrate security functions that can be integrated with the SD-WAN platform.
Managing how these functions work together may seem straightforward – but there are many different approaches. SASE and secure SSE approaches have nuanced differences and architectures (cloud-based vs. on-premises approaches). How they are implemented can vary depending on the type of organizations, use cases, and management system desired.
Start with the Integration Needs
In the long run, the integration of SD-WAN, SASE, and SSE technologies is good for end users, as it helps unify their networking and security architectures. But, in the meantime, there has been an explosion of vendors and marketing – making it all a bit confusing. Let’s try to clarify what’s happening from the end-user’s perspective.
As a start, network and security managers should first take inventory of their existing security and networking platforms, and then figure out how best to integrate these with a singular platform that can help them manage and integrate any of the SASE or SSE functions they need. The needs will vary based on their specific network architecture and implementation.
Based on our surveys and interviews with end users, there is a growing demand for improved integration of cloud and network security tools to adapt to factors such as end-user mobility, increased access to cloud applications, and diverse security threats. The difference on how to do this will come down to specific approaches to integrate these functions. There are basically three possibilities.
- Single-vendor platform including all SASE components coming from the same vendor
- Mix-and-match a collection of functions in a custom integration for do-it-yourself (DIY)
- Adopt Integrated SD-WAN and SEE solution with integrated management plane and a single policy repository for network and security policy
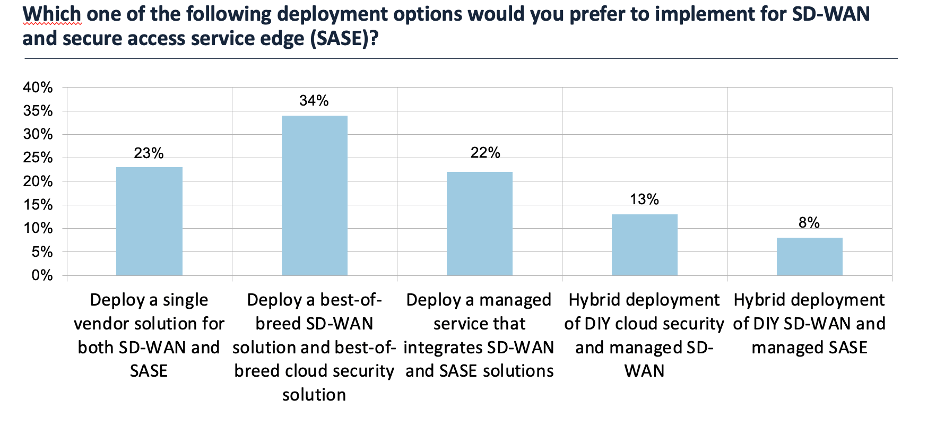
While some clients will pursue a single stack, our research shows that most customers are pursuing best of breed. The chart below shows the results of a question about SASE and SD-WAN deployment options in a survey of 196 networking and security management professionals, conducted by Futuriom in March. Although the combination of best-of-breed SD-WAN and security solutions was the most popular selection, with 34% of respondents embracing that option, the wide distribution of results show that the market demands flexibility.
Having choice is a good thing. To this end, some vendors are pursuing of providing the best of both worlds – flexible integration of best of breed, or single stack. For example, Aruba now offers “choice or flexibility” for either single-stack, unified SASE (with the Axis acquisition) or a flexible way to integrate third part security.
Multicloud Also Part of the Puzzle
There are other considerations. For example, where does multicloud come in? Increasingly, organizations are leveraging cloud infrastructure, where they can cannot more quickly to cloud services and networks at local points of presence (PoPs). A correct SASE architecture should also take this into account. For example, does the platform also enable management of multicloud connectivity and security?
The SASE platform, after all, should include the capability to orchestrate and connect multicloud and networking functionality – as well as adding third-party capabilities. It’s important to look at technologies and vendors that have a flexible vision of the future that also include multicloud vision.
There’s also campus environments. Imagine a network extending from the enterprise campus to the cloud, and the security needs in between. The network now needs to connect this wide variety of services and applications in a fast and simple way, with security built into the network. It should also be able to extract enough information about applications and context to ensure a high-quality experience. This includes the capability to inspect traffic and have full visibility of applications.
Many of the technology vendors in the SASE and SSE areas might not connect these dots. There’s no reason that these environments should be seen as islands with separate management systems that can’t orchestrate or connect SASE, SSE, or multicloud networks as well.
HPE and Aruba have always had a pragmatic vision of SASE and SSE, seeking to blend integrated management, ease-of-use, and best-of-breed functionality. This includes enabling end users to adopt third-party SASE and SSE functionality while using Aruba’s EdgeConnect platform to orchestrate and manage these functions. Better yet, Aruba’s ClearPass cloud authentication and campus networking platforms mean that one management platform can be used for all these functions. Even third-party best-of-breed platforms can be managed from a single, cloud-based management system.
If our vision of networking and security platforms is correct, end users should look for fully featured, SASE platforms – rather than isolated SSE point solutions. That way, they won’t risk being stranded on a SASE or SSE island.




