
Probably the best part of my role is learning how our many and different customers go about securing their networks and data. I was recently meant to present to a large vehicle manufacturer on ClearPass's integration with MDM/EMM solutions, but instead, the client presented me with their view to securing a large mobile workforce. With their permission, I'll share their ideas for securing their mobile estate, where a large MDM architecture or investment was not used.
Approximately 100,000 employees and 75,000 work in their manufacturing plants. A further 15,000 work in design and testing, with the remaining 10,000 are in executive functions like management and marketing. Based in Europe they are subject to substantial workers council obligations which make it more interesting culturally to use BYOD, as they have to negotiate what the enterprise can and cannot do on employee's devices.
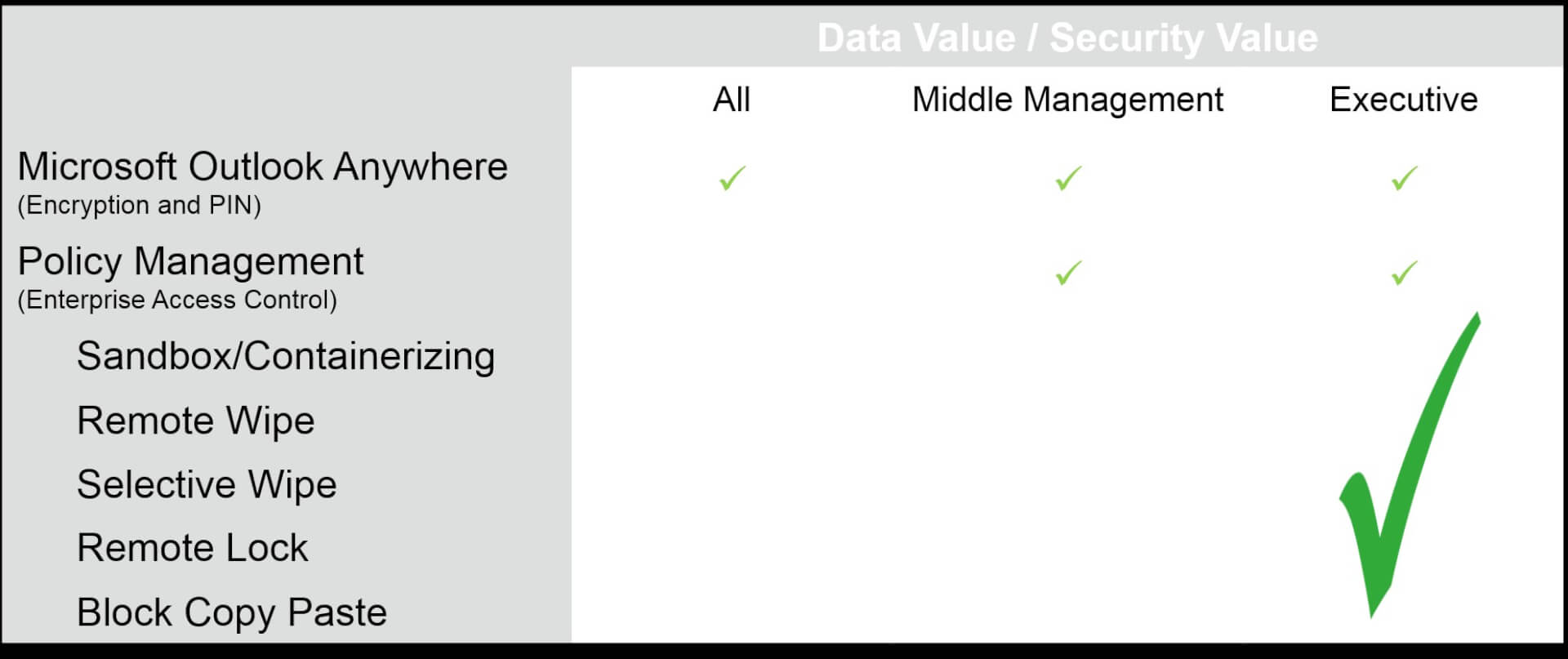
The Production Line. There is not much information sent to the manufacturing team that would be subject to privacy standards or of interest in corporate espionage. However, the company still wanted to offer BYOD to effectively communicate with a major part of the organization that does not use a corporate device on a daily basis. A calendar is a useful tool for scheduling shifts as it is setting up meetings. Additionally, there is some limited location tracking that made BYOD devices suitable as alternatives to time cards.
The only requirements they initiated were that the device must be encrypted (no specific encryption for corporate data) and a PIN or fingerprint should be used to secure the device.
Middle Management. Comprised mainly of operational management, the company evaluated the data they processed on mobile devices and realized that little data was input or managed on the devices. The devices were mainly used for corporate applications, such as ERP and CRM. They did not wish to stop the use of applications, but they wanted to limit their use by the device, location and time.
With this in mind, they decided to use the same policy they initiated for the production line – Encryption and PIN, but they added an application control posture. Depending on the person's role, they may access the applications on a corporate tablet, or on BYOD if on a corporate Wi-Fi connection. They imposed fewer rules on corporate laptops, where they could be assured of endpoint security tools.
Executive Level. More specifically, those who are involved in the design, performance and marketing that potentially have a look into the future of the organization and its intellectual property needed different attention. For those 10,000 employee's they were free to use their own devices for work – smartphone, tablet, etc., however, they were required to use the enterprise MDM solution.
Beyond the above examples (and in the below chart), they wanted to ensure that in the case of a lost device, they could specifically delete the business portion of the now sandboxed device, and get confirmation that the data was gone. In addition, they wanted the ability to restrict copy/paste functions between corporate and personal applications.
So that's what they wanted to achieve and the policy they wanted to implement, so how did they achieve their goals?
With relative simplicity.
For the Production Line employees they utilized the Microsoft Outlook Anywhere policy engine to ensure that upon signup, users would have to enable native encryption and a PIN or fingerprint on the device. They also educated users on the Wi-Fi backup process they could utilize to backup photos to the Google and Apple clouds, to prevent unhappiness in the event of device loss.
For middle management, they leveraged their existing wired and wireless Network Access Control (NAC) solution, ClearPass, using Onboard to associate users to devices. With ClearPass sitting at the heart of their authentication process, their policy management program extends to controlling what applications and application data a user and his or her device can access, with a variety of usable contexts – device ownership, connectivity type, location or time.
Their policy suggests there are good reasons for not allowing a BYOD tablet belonging to a European Director to access the ERP Finance application while in China, at 2am. By defining what is acceptable, it automates the process of securing the infrastructure without a burden on employee productivity. They secure the way employee's work, not requiring them to bend to an oppressive security architecture. Users will often manufacture a solution to perceived productivity interference, that often creates greater risk. All of this is achieved without an MDM solution.
Finally, for the executive team they had decided to work with MobileIron for their MDM solution. ClearPass Onboard was used to determine user and device eligibility, and to ensure a speedy, automated configuration of the device. The additional value comes from policy enforcement. If a user removes the MDM software, jailbreaks a device or commits another compliance breach, the MDM solution, informs ClearPass via the ClearPass Exchange API, and the device is suspended from the enterprise. In the case of smartphones, an automated SMS is sent with instructions to become compliant and reconnected.
All with zero resources from IT or Security
They have put together a wonderful, low cost managed solution, unique to their needs. They took the time to analyze their risk, understand their potential exposure and pragmatically mixed policy and technology to secure their enterprise.




