
Today, a lot of people are blindly applying blockchain to every problem they see. But blockchain should only be applied to problems which are caused by the centralized nature of the current architecture and is desperately in need of an architectural revamp. For example, intermediaries getting access to the sensitive data of users because they are the centralized custodians of user identity, resulting in avoidable access and storage of personal information and causing concerns about data usage and data breaches.
Cybersecurity is an area that lives and breaths trust. The triad of confidentiality, integrity and availability are its founding stones. Naturally cybersecurity’s problems are closely related to trust and privacy. So, there is a natural fit for some of the unsolved problems of cybersecurity with blockchain.
In this blog, we will look at the top four cybersecurity problems which blockchain can assist in solving, because the centralized nature of the current architecture in these areas is the root cause of resultant trust, privacy and security concerns. We will also look at technical developments taking place in corresponding areas.
Top 4 Security Issues Due to Centralized Architectures
- Identity: Highly centralized identity systems leading to centralization of data with identity provider platforms, resulting in privacy violation of users. Solution: Decentralized identity
- DNS: Centralized DNS and attacks. Solution: Distributed DNS
- IoT Trust: How do I trust an IoT device? Solution: Trusted things
- Privacy: Can I share information about me on need-to-know basis with high level of privacy and control to a digital gatekeeper or a verifier or an intermediary? Solution: Verifiable claims
Using Blockchain for Decentralized Identity
With single sign-on (SSO) and social sign-on, identity is highly centralized in today’s world. But the resulting problem is privacy. When identity is provided by single centralized entity, all the authentication and user access data resides with that central entity. This information can be used for profiling and can be sold without consent of the user, which has unfortunately happened in the past.
So, there is a disruption emerging in the identity space, where identity is decentralized and user owns the identity completely on a public or private blockchain, based on the business requirement.
The first advance is decentralized public key infrastructure (DPKI), where blockchain can be a platform to prove your identity. Participants on registration will get an identity called a decentralized identifier (DID). Their public key will be available to on the blockchain as a proof and the users will hold their private key.
On top of DID, other decentralized applications like decentralized key management system, DID authentication and verifiable claims are being developed. This is a fundamental and much-needed disruption to the way we are known in the Internet world.
Using Blockchain for Distributed DNS
DNS is one of the most important Internet services and is centralized. We are trusting that someone will maintain the IP-to-domain name mapping correctly, will provide us the right data to us on time and are just consuming the response. This is bound to be disrupted for its own good. The majority of the DNS attacks are based on attacking the centralized DNS server as it is a small and potentially high-reward attack surface. Some examples are domain hijacking and DDoS attacks on DNS servers.
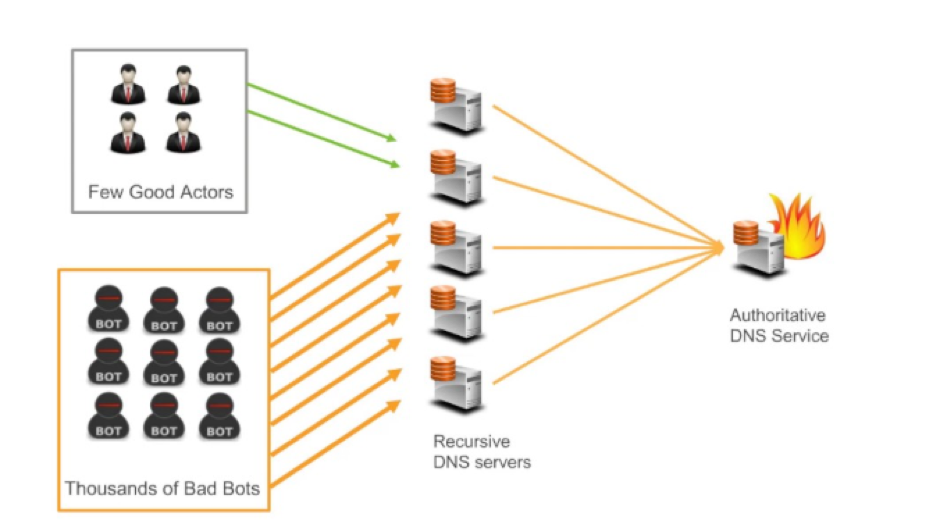
Image courtesy of AWS Online Tech Talk
Since blockchain-based domain name servers will be distributed and have consensus-based storage, attacking a single server will be useless. To launch a domain hijacking attack, the attacker has to successfully attack at least more than 50% of the distributed DNS servers in the world to make the change, which is highly difficult. The DID resolution draft reportby the World Wide Web Consortium (W3C) and Ethereum Name Serviceare couple of examples of key developments in this area.
Using Blockchain for Verifiable Claims
The closest equivalent in the physical world for verifiable claims are coupons or passes. Verifiable claims do not disclose any information about the holder, but verify that the receiver should be give right consideration as promised without sharing any additional knowledge. Verifiable claims are so powerful in this post-GDPR world and can replace using complete identity in a lot of cases.
Rather than using identity, we may be issued verifiable claims for graduation certificates, bank balances, salary certificates, driver licenses, visas and much more. Not just for people, verifiable claims can be issued for things as well. W3C created a verifiable claims data modeland it is one of the potentially most disruptive applications of blockchain in the next couple of years.
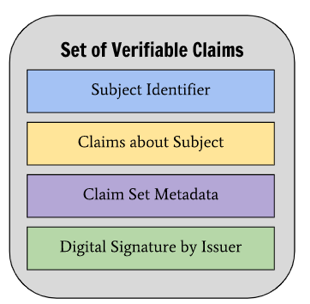
Image Courtesy of W3C
Using Blockchain for Trusted Things
The biggest challenge for Internet of Things (IoT) is security, resulting in uncertainty around trustworthiness for doing a transaction with it or allowing its traffic or depending on its data. There are technologies evolving in the areas of decentralized identity for things as dependent identity of a person or an organization, verifiable claims that IoT devices can own, verifiable software, which can be validated to ensure that no malicious changes have been made before execution, and a trusted execution environment, which can help ensure at the microprocessor level that no changes are made to security-related information stored in an isolated environment, especially identity keys and critical software.
Disrupt or Be Disrupted
Blockchain has a major role to play in the world of cybersecurity. The more a specific function gets centralized, the greater the probability of a security attack and hence the higher the potential of a decentralized disruption. Security companies and start-ups in the space have just two options: Be the disrupter or be disrupted. It’s just a matter of time!
Read More in My Blockchain Series
10 Blockchain and New Age Security Attacks You Should Know
Enterprise Standards Blockchain Collaboration
Tools for Developing Real-World Enterprise Blockchain Applications
Blockchain: Do You Have an Identity Problem?
GDPR: Control Over My Personal Data, My Right




