Posts with tag "Machine Learning"
Federal Cybersecurity Threats Demand an Analytics-Driven Detection and Response
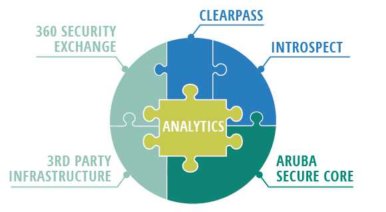
Aruba 360 Secure Fabric delivers 360-degress of analytics-driven, active cyber protection and secure access.
GDPR: Control Over My Personal Data, My Fundamental Right
Understand the far-ranging impact of the European Union’s new privacy law going into effect in May.
(HPE) Aruba Named a Leader in Gartner’s Magic Quadrant for Wired &...
We believe everyone wants to be a Leader in Gartner's Magic Quadrant. Being there tells the world you have both completeness of vision and ability to execute. So we're delighted to find ourselves positioned...
CISO’s Guide: 9 Machine Learning Terms You Must Know
In our previous blogs, we introduced the concept of machine learning for cybersecurity , then took a deeper dive into the pillars of machine learning and explored how supervised and unsupervised machine...
Cybercriminals Target K-12 Student Data
It’s time to step up IT security defenses against disruption and extortion of our schools.
CISO’s Guide: Principles of Machine Learning
Take a deeper dive into how machine learning can detect cyber attacks faster.
3 Reasons Why Machine Learning is Not a Cybersecurity Pipe Dream
Despite skepticism about machine learning's role in security, organizations can benefit from machine intelligence when combatting sophisticated attacks. While some believe that machine learning is...
CISO’s Guide: Introduction to Machine Learning for Cybersecurity
We explain the overall cybersecurity situation and why machine learning can help.
Horses, Barn Doors and Ransomware
There is a favorite saying to characterize a situation where the remedy to a problem shows up too late: "It's like locking the barn door after the horse is stolen." When we look at how many user and entity...
Understanding IntroSpect’s Modular, Data-Agnostic and Scalable UEBA Architecture...
Understand how machine learning complements security analysts' need for behavioral analytics.