Collaboration is a hallmark of today's digital workplace and has become business-critical for enterprises. And the possibilities for collaboration are exponentially greater than they were a generation ago. Businesses are global and employees are mobile -- and always-on. Real-time sharing, remote access to desktops, voice-over-IP, instant messaging, and cloud-based collaboration are all normal ways of working that put many valuable corporate assets online and within reach of bad actors.
Collaborative digital workplaces require a level of security not implemented by many organizations. Securing identities, data, source code, and other intellectual property is much more difficult because mobile, cloud, and IoT have radically changed the security perimeter.
![8320_Social_Card_360_Partha_Blog_V2_1116x595[13].png](https://media.arubanetworks.com/blogs/31654i550E77AE5D3B71DE.png) The Vanishing Perimeter
The Vanishing Perimeter
![]() First, Wi-Fi networks have moved the network perimeter beyond the building perimeter. In the past, employees and visitors had to pass through security to enter a building and use its network. But Wi-Fi extends the network perimeter into parking lots, across streets, and even into other buildings. In addition, many of today's mobile workers are using their own personal devices. BYOD is well established in many organizations, but the security challenges never get old. BYOD moves or even eliminates, the security perimeter. It used to be, you could not do work unless you were in the building at your desk. The desktop environment could be locked down. But with BYOD, malware can walk in through the front door on a personal device and then gain access to the corporate network. And what's more, business data and personal information are both being sent across the same networks.
First, Wi-Fi networks have moved the network perimeter beyond the building perimeter. In the past, employees and visitors had to pass through security to enter a building and use its network. But Wi-Fi extends the network perimeter into parking lots, across streets, and even into other buildings. In addition, many of today's mobile workers are using their own personal devices. BYOD is well established in many organizations, but the security challenges never get old. BYOD moves or even eliminates, the security perimeter. It used to be, you could not do work unless you were in the building at your desk. The desktop environment could be locked down. But with BYOD, malware can walk in through the front door on a personal device and then gain access to the corporate network. And what's more, business data and personal information are both being sent across the same networks.
Second, many enterprise applications are consumed directly from the cloud. These direct-to-the-internet pathways don't pass through the traditional enterprise network protections and create new risks that old tools can't address. Most security technologies deployed today are perimeter-based and not designed for cloud-oriented threats.
Third, the advent of the Internet of Things (IoT) is bringing thousands of often inherently insecure sensors and other devices into corporate networks. These devices may be on moveable equipment, attached to a company's building, or given to employees. "Things" can be rogue devices connected to open ports on the network and often times go undetected by IT. These "things" also don't have the compute power to protect themselves with endpoint security software such as anti-malware.
When the physical perimeter is no longer the network perimeter and threats can enter from the inside, the old ideas of trust don't apply. Today, siloed protection is no longer enough. Security must be built into the network infrastructure and act as a fabric that integrates network, access, device, and user security.
The Aruba 360 Secure Fabric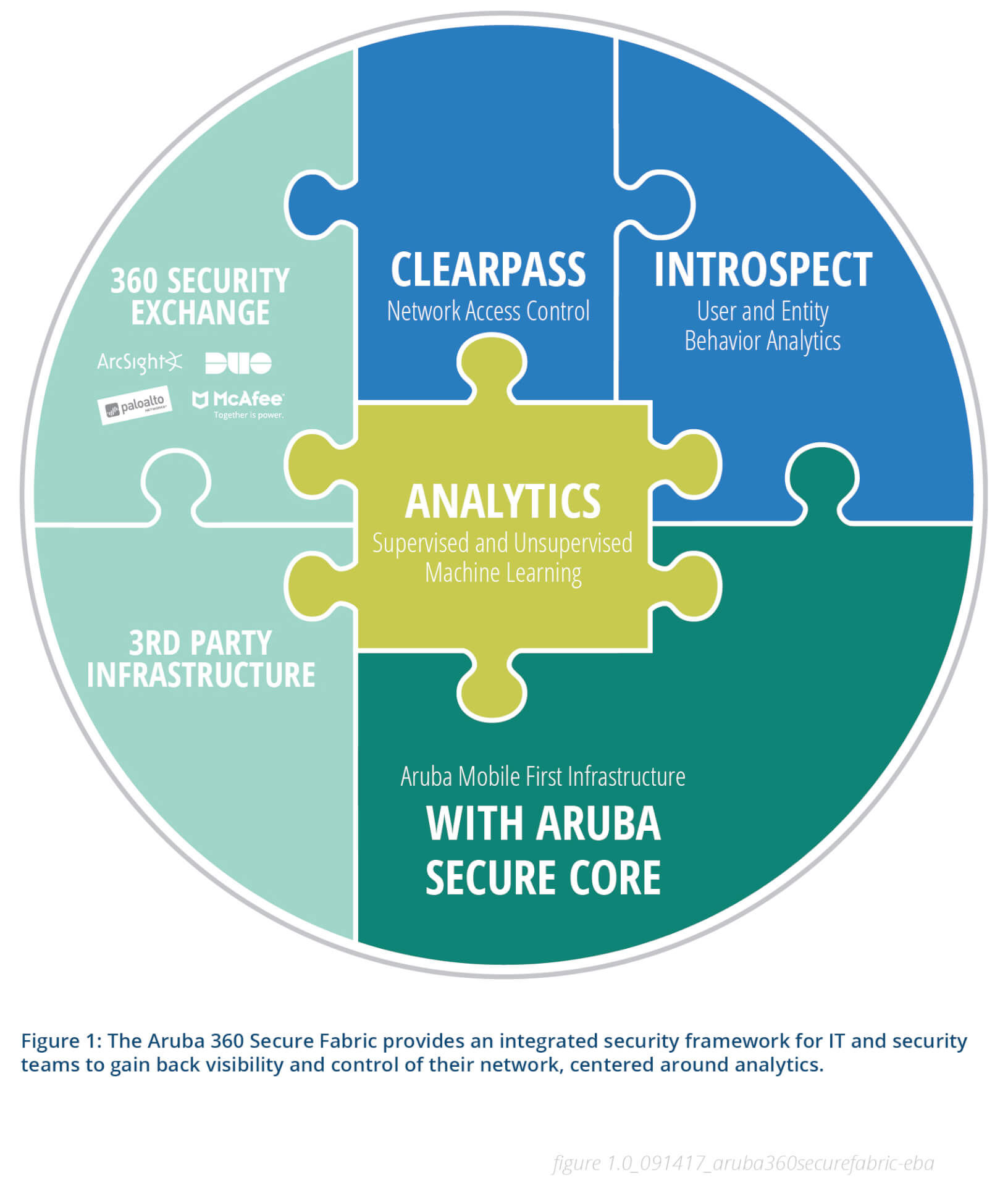
We at Aruba took a unique design approach with our Aruba 360 Secure Fabric. Starting at the infrastructure layer, we embedded the Aruba Secure Core into the network. The Secure Core is the inherent security built into every Aruba AP, mobility controller, and switch. Secure Core utilizes security technologies such as secure boot, encryption, deep-packet inspection (DPI), VPN, IPS, and firewall technologies to ensure that the network devices and the traffic that passes through them can be trusted.
SecureCore brings the infrastructure into a trusted state. And SecureCore allows the network to act as a sensor, giving off critical data that you can trust about every user, every device connected, and the nature of the traffic that passes through them using technologies such as DPI. The network as a sensor feeds the unique analytics capability that only Aruba infrastructure can provide.
Our security software can overlay any network and utilizes the network data to gain security insights to allow for policy-based action taking. Starting with ClearPass, you set up the network with the policies you want. ClearPass lets you segment the devices themselves and not rely only on network segmentation, as in a VLAN. In this way malware can be prevented from propagating laterally, hopping across the network to get to higher value assets.
There's one more major problem. As the network perimeter has enlarged and grown more diffuse, new classes of user devices and other things like security cameras must be observed. There is so much to keep track of, in fact, that the problem of dealing with too much information is very real. With so much information, the occurrence of false positives can quickly overwhelm traditional methods of defense and the security teams who are responsible for investigation and response
What's needed is a big data analytics platform that leverages machine learning to spot anomalies and connect the dots, weeding out false positives to determine what might be a real problem. This is exactly what IntroSpect does. IntroSpect is User and Entity Behavior Analytics (UEBA) technology that we gained from our acquisition of Niara.
But still, more is needed. When a likely problem is found, it must be immediately isolated, so that your network and systems are protected. Then you need to study it to learn just how serious it is. That is where IntroSpect integration with ClearPass comes in. You can instruct ClearPass to quarantine the suspected device and keep it from talking to other devices on the network. And ClearPass programs the infrastructure to get more data from the device and send it for further analysis.
The recent WannaCry ransomware outbreak got everyone's attention. Here's how IntroSpect and ClearPass technologies can combine to protect organizations from outbreaks like WannaCry: After a machine is compromised, it seeks to communicate with the attacker via its command and control (C&C) channel, in the case of WannaCry, via the Domain Generation Algorithm (DGA) technique. But IntroSpect detects this because it has been trained with over 1 million known DGA domains collected from 30 different families such as Zeus, Cryptolocker, and Conficker.
Each system compromised by WannaCry also acts as a bot, scanning over the enterprise network to find other vulnerable systems. But IntroSpect monitors and profiles the normal baseline behavior of each machine and detects anomalous behavior such as scanning. When an anomaly is detected, an alert can be automatically sent to ClearPass, which can be programmed to take systems suspected of infection off the network, where they can be studied and treated without infecting any other systems.
All this occurs in the context of a security fabric that we call the Aruba 360 Secure Fabric, giving enterprises 360 degrees of active cyber protection for any network. It encompasses Aruba technologies, of course, but also important security technologies provided by other vendors such as McAfee, ArcSight, Palo Alto Networks, and Duo Security that integrate through the Aruba 360 Secure Exchange.
We also integrate with network infrastructure from vendors such as Cisco and Juniper Networks.
Without this kind of simplified and end-to-end security, the collaborative enterprise will quickly disintegrate. Corporate confidentiality will disappear, breaches will increase, and the cost of attempting to protect data -- unsuccessfully, in all probability -- will become astronomical.
There is no going back to the security perimeters of yesteryear. Never again will we do all our work in self-contained, secure buildings. Businesses are global and employees are mobile. But under the umbrella of the Aruba 360 Secure Fabric, your organization is safe to freely explore exciting new horizons of being digital.




