Two months back I posted an article on 4 Ways to Safeguard your Guest Network. While those four suggestions still very much apply, I stated that shared key security on guest networks is ineffective. Fortunately technology is never stagnant and new features frequently address old pain points. So I'm back again with a new alternative.
Deploying guest network WPA2 security with shared trivial passwords is now possible utilizing a new feature introduced in ClearPass 6.4 called EAP-PEAP-Public. EAP-PEAP-Public provides WPA2-Enterprise level security with pre-shared key simplicity for your guest network.
EAP-PEAP-Public has a number of benefits that PSKs just can't match:
- The session encryption key (a.k.a. pairwise transient key) derivation is significantly more robust. Use of 802.1x ensures that those keys periodically rotate. Unlike WPA2-PSK, the EAP-PEAP-Public session keys do not exclusively rely on mac address and nonce values (easily sniffed), SSID name (known) and the PSK passphrase (presumably posted in the guest venue) for creation.
- WPA2-Enterprise is not susceptible to rainbow table attacks like its PSK little brother
- Your credentials can actually be simple and readable by a human, without degraded security!
- Support for EAP-PEAP-Public is built into most modern day operating systems (iOS, Android, Windows 7/8, OSX). More importantly it's easy-to-use even for your least technical-savvy user.
- It's simple to configure within ClearPass 6.4. Select a few options and you're running.
What about other options such as dynamic PSKs? In practice those implementations often have issues with scaling, performance and inter-AP roaming problems - particularly for larger guest network deployments. And users still need to deal with a maddening non-sensible PSK string.
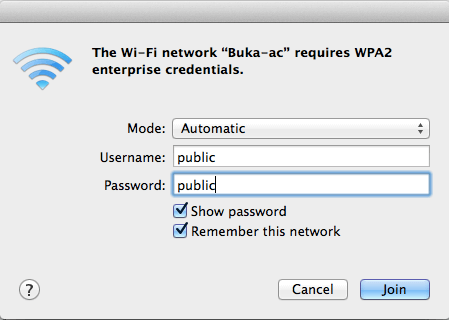
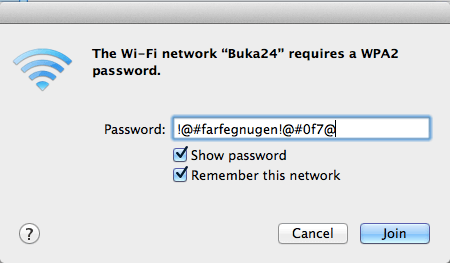
What do you think your guest prefers?
All being said, EAP-PEAP-Public still doesn't fully protect your network from a man-in-the-middle style attack, as gstefanick describes in his excellent blog post earlier this week. So make sure your SSID names are unique and your WIDS system is scanning for rogue APs.
Is your organization striving for additional guest security capabilities beyond captive portal per user auth? Well you now have a simplified and effective solution at your disposal with ClearPass.
Check out our Next Generation Guest Access for #GenMobile guide for more security best practices.




