Operational technology (OT), including industrial control systems (ICS) and supervisory control and data acquisition (SCADA), is used to directly monitor and control critical infrastructure for energy, telecommunications, water and waste. These complex systems are essential for generators, pumps, valves, actuators and other equipment that run industrial systems.
Growing OT Security Challenges
Historically, industrial systems used proprietary, non-IT protocols and were isolated from the Internet. Stringent physical controls were usually in place to deter any potential cyberattacks. However, this once-isolated world has evolved dramatically.
Industrial systems are now being connected to enterprise networks and the cloud to leverage big data, predictive maintenance and smart analytics. Companies are adopting new capabilities and efficiencies through technological integrations to gain a competitive advantage.
The IT-OT convergence brings new security risks, such as lack of proper asset inventory, no visibility into OT behaviors, and a lack of security controls. Access control lists (ACLs) are unmanageable (if they even exist) and standard enterprise security tools, such as firewalls and network access control, do not have any visibility or understanding of the OT network.
Understanding the IT-OT Risk
According to the CyberX Global ICS & IIoT Risk Report 2020 report, we see staggering numbers of vulnerabilities in production ICS systems that threaten business survivability.
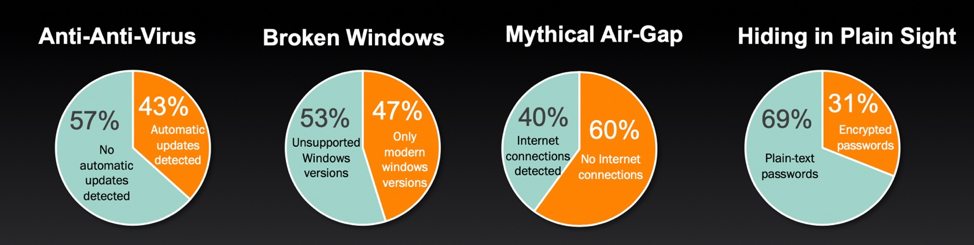
The CyberX study is based on 850+ production ICS networks across six continents and all sectors (energy and utilities, oil and gas, pharmaceuticals, chemicals, manufacturing and mining). Read the full study.
Industrial control systems are usually high cost and demand 100% uptime. It would be a diaster to communities and even a country’s economy if critical infrastructure services were attacked.
The challenge is amplified with regulatory, safety and compliance requirements to safeguard such systems, such as Singapore’s IMDA IoT Cyber Security Guide, which strengthens the protection of critical infrastructure against cyberattacks, or Japan’s efforts to strengthen cybersecurity measures in advance of the 2020 Tokyo Olympic Games.
Start with a Security Framework
Organizations wanting to strengthen OT security can start by incorporating guidelines from the NIST special publication 800-82 Guide to Industrial Control Systems (ICS) Security into their security frameworks.
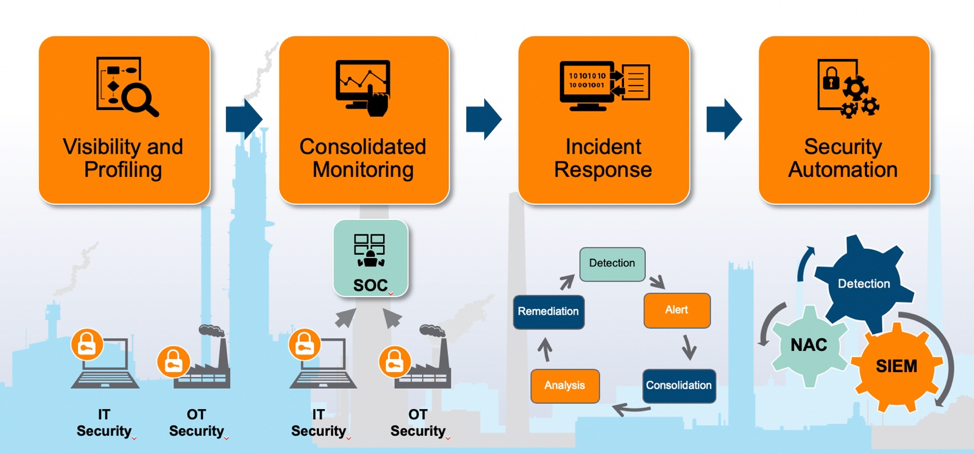
Maturity of OT/ICS security in an organization.
Leverage Security Automation to Ensure Continued Operations
Aruba, together with OT security vendors such as CyberX, provide solutions at each step of the maturity model from complete visibility into network control traffic and comprehensive monitoring and technical controls to applying the right security policies.
With our joint solution, security automation can be put in place to quarantine and block devices based on detected zero-day threats. The solution can remediate machines with outdated or noncompliant software and deploy remediation policies for controllers running firmware with known vulnerabilities.
It is critical to have an OT strategy in line with a security framework in place to protect both the enterprise and ICS environment, ultimately reducing security vulnerabilities and incidents to maintain business continuity.
Get more information on the joint Aruba and CyberX solution.