 Have you ever looked at those authentication options on your SSID and wondered, “What is the difference between WPA, WPA2 and Enterprise?” If you do a quick search, you’re sure to find statements like, “Meh, they’re all compatible, it just depends on the options you see for the SSID.” There’s some truth to that, but really, if they were all the same why do they function so differently? The devil is in the details.
Have you ever looked at those authentication options on your SSID and wondered, “What is the difference between WPA, WPA2 and Enterprise?” If you do a quick search, you’re sure to find statements like, “Meh, they’re all compatible, it just depends on the options you see for the SSID.” There’s some truth to that, but really, if they were all the same why do they function so differently? The devil is in the details.
I don’t want to discuss the encryption or lack thereof with WEP and Open authentication. We need to secure our networks—in most instances—so these technologies should be dead and gone. Outside of guest access, we need to make our wireless environment available, stable, and secure. A brief description of the wireless authentication options at your disposal are WPA, WPA2-Personal and WPA2-Enterprise. I’ll address certificates in a moment.
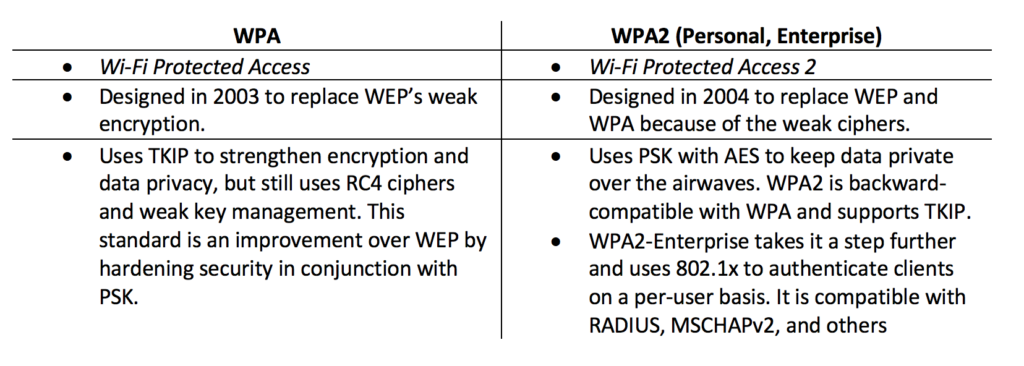 Some of these acronyms can be confusing. The problem is that if you aren’t sure what these things do, the authentication design for your wireless clients could be insecure and hard to manage. At the risk of making this post read like a dictionary, I think it’s very important to understand the uses.
Some of these acronyms can be confusing. The problem is that if you aren’t sure what these things do, the authentication design for your wireless clients could be insecure and hard to manage. At the risk of making this post read like a dictionary, I think it’s very important to understand the uses.
- Pre-Shared Key (PSK): PSK is a password assigned by administrators for an SSID. The user will add this password to their wireless configuration so they can complete the wireless connection setup. It’s used when you don’t control access to wireless by user, and still want security for that access. It’s what you would use on your home network or in a public establishment, like a pub or restaurant.
- Temporal Key Integrity Protocol (TKIP): TKIPis an encryption “wrapper” for the WEP standard. Each frame is encrypted with a 128-bit block on a frame-by-frame basis using a unique key on each frame; that’s the temporal part of this protocol. The 40-bit RC4 algorithm was developed for WEP and was easily compromised and TKIP tries to overcome the weak algorithm.
- Advanced Encryption Standard (AES): AES is an encryption algorithm using 128-, 192- or 256-bit block lengths to generate the encryption keys. The key size is actually unlimited and only one key is required for encryption and decryption because it’s a symmetric algorithm. AES is pretty much a standard for key generation and is supposed to provide data security for 20-30 years. Mileage may vary on the “years” as technology changes.
What About Certificates?
If you run an enterprise-class network where you can provide certificates (e.g. Microsoft’s Active Directory), you have a couple of options available. With Microsoft Active Directory, for example, there are two certificates in use on the enterprise network: machine and user certs. There are pros and cons of each, so you’ll want to consider your security posture, device and user management workflows.
The way an Active Directory scenario works is logically simple, but mechanically complex. Your administrator creates and joins an account for both the user and the computer. When these connect to the domain, the domain controller creates and signs both certificates. The controller attaches the cert to the user and machine account. This lets the domain controller know that everyone is good to play on the domain and has certain permissions. It basically validates the user and machine.
If you think about this workflow, your company created them so you should trust both the user and the machine attaching to the network.
When to Worry About It
Which method should you use? For guest access, I suggest that it depends on your overall network architecture – surprise! If you want to give Open authentication to your guests (i.e. a coffee shop, pub or conference room), I’m of the opinion that you segregate that traffic on different hardware if possible. Again, it depends on your security posture. I don’t like having trusted and untrusted traffic mixing together if I can avoid it.
With guest access, there are options with either capture portals or lobbies. With a capture portal you can force your guests to enter a valid email address or phone number before they are allowed onto your network. Once they receive the authentication code from the wireless system, they simply enter in the code and are given access for a period you specify. With a wireless lobby, a designee of the company can create or approve a guest account. Where your employer stands on this issue is for you to discuss.
Do you have a method of deploying certificates in your organization? Do you have a lot of IoT devices? I would recommend using machine certificate authentication. With IoT, you are mainly interested in whether or not you control the device and since there’s no user authentication, it’s a great option. If you provide smartphones or tablets to your employees, you likely don’t mind they join your wireless network. These are also devices which would require a machine certificate rather than a user cert.
Disconnecting These Thoughts
With all these ways to authenticate users, you may ask yourself, “What is the best way?” I’d say that’s a great question. You really need to consider the nature of your business. The problem is so many aren’t sure of all the mechanics behind this service. Even basic concepts don’t seem so basic when you read about them, then try to set up the service.
Related Content
Understanding Encryption Types
802.11i Authentication Overview
Read My Other Blogs
Cutting the Cable: Where Do You Start?
Wireless Design: Turn up the Heat(map)
Voice over Wi-Fi Doesn't Have to Be Trouble
Understanding Wi-Fi Authentication




