
An advertising campaign from the 1980’s posited that peanut butter and chocolate were “two great tastes that taste great together.” While confectionary tastes may vary, there’s no denying that some things just work better together. When it comes to IT security, network access control and Zero Trust security are like peanut butter and chocolate—great on their own, undeniably better together.
Network access control vs. Zero Trust security
Network access control and Zero Trust security are not the same, but they are related.
Zero Trust security is an IT framework in which no device or user is trusted by default. Instead, each subject must demonstrate its trustworthiness to gain access to just the resources needed to do its job or fulfill its function—a paradigm referred to as least-privilege access. Trustworthiness is continuously monitored and if a subject demonstrates anomalous or suspicious behavior, access can be limited or revoked. This dynamically assessed, limited role-based security can help minimize and even prevent lateral spread of attacks.
Network access control (NAC) solutions provide the technology to enact this model of continuously monitored least-privilege access. NAC solutions comprise capabilities across several dimensions, including:
- Visibility into who and what is on the network and what they are trying to access
- Authentication of users and devices against known profiles
- Rule-writing, for translating business and functional intent into network access policy and conditions
- Authorization, for applying the appropriate policy to users and devices
- Policy enforcement that allows, denies, modifies, or revokes access
- Monitoring for changes in user or device behaviors
- Logging and reporting to provide accurate alerts and historical reporting of user, device, and network activity
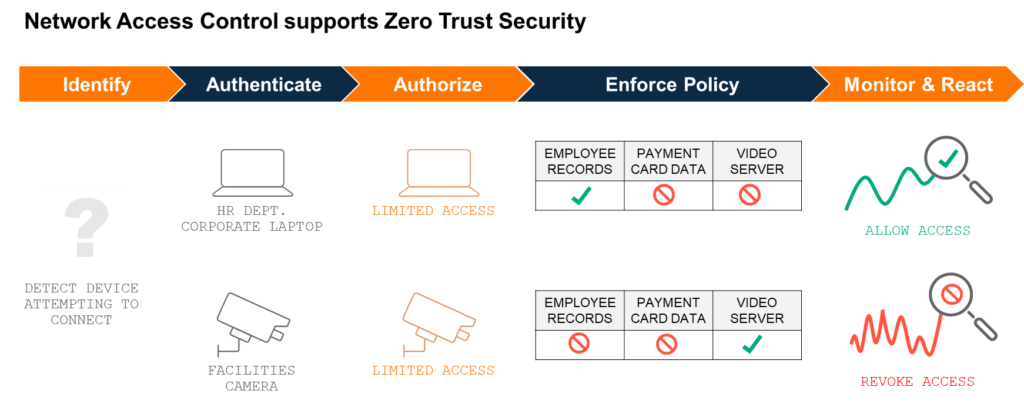
NAC solutions can deliver least-privilege access to resources, a foundational element of Zero Trust security strategies.
Uses for network access control in Zero Trust security environments
NAC solutions can be helpful for addressing several security challenges within a Zero Trust environment. Here are some examples:
- Guest access: Visitors to sports stadiums, amusement parks, retail shops, and other campus and branch environments expect Wi-Fi connectivity during their stay, yet IT teams need to ensure those untrusted users do not introduce vulnerabilities onto the network or access restricted resources. NAC solutions can provide streamlined workflows for guest registration and appropriate levels of access.
- Privacy and compliance: Organizations often need to adhere to data privacy and protection mandates that restrict access to sensitive data, like the Health Insurance Portability and Accountability Act (HIPAA) and General Data Protection Regulation (GDPR). NAC solutions can ensure that only authorized users within organizations can access information like patient health records, payment card data, and consumer personally identifiable information (PII).
- Internet of Things (IoT): More and more IoT devices like HVAC controllers, surveillance cameras, infusion pumps, and automated guided vehicles are being connected to enterprise networks. These devices can be used in cyber-attacks, making it critical that their exposure to resources on the network is limited. NAC solutions can provide visibility of IoT devices on the network, monitor their behavior, and quarantine devices observed to be participating in an attack.
ClearPass Device Insight is one of several ways HPE Aruba Networking provides visibility to support network security management, no matter what kind of devices are connecting and where they're connecting from. Learn how.
Explore network access control and Zero Trust security in depth
These resources can help you learn more about NAC solutions and how Aruba can help you support Zero Trust security strategies:




