As an ethical hacker or cybersecurity specialist, I am often asked what is the most important thing when it comes to an organization’s cybersecurity program, and what can we do to make sure our security culture is focused effectively? To the surprise of most, I say user experience. I couldn’t tell you the number of cybersecurity teams I have come across throughout my career who are absolutely exhausted trying to keep up. The issues aren’t solely about available analysts, budget, controls, etc. Often, there is a major concern that cybersecurity teams are rarely equipped to handle: user acceptance.
Users are the Weakest Link
Unfortunately, users are easily blamed for not following policies, or not using the controls in place to protect them. But if you look just a bit closer, you might ask yourself, why? The answer to that question often comes down to the fact that the processes in place are too complex or they simply don’t work effectively. Ultimately, going around the controls or practices in place is easier than following them.
If you’ve ever worked in a tech support team, you’re likely familiar with the term shadow IT. Shadow IT is a term that encapsulates all that is not documented or expected to be found within an organization – e.g. those quick fixes. After all, at the end of the day, users need technology to just work to do their job efficiently. Shadow IT is a result of non-tailored, user-friendly effective solutions.
To minimize insecure shadow IT creeping into an organization, I always advise to look at how employees work and what we can do to enhance that. Let’s fix the problems before they arise and build secure solutions that just work. Seems logical, right?
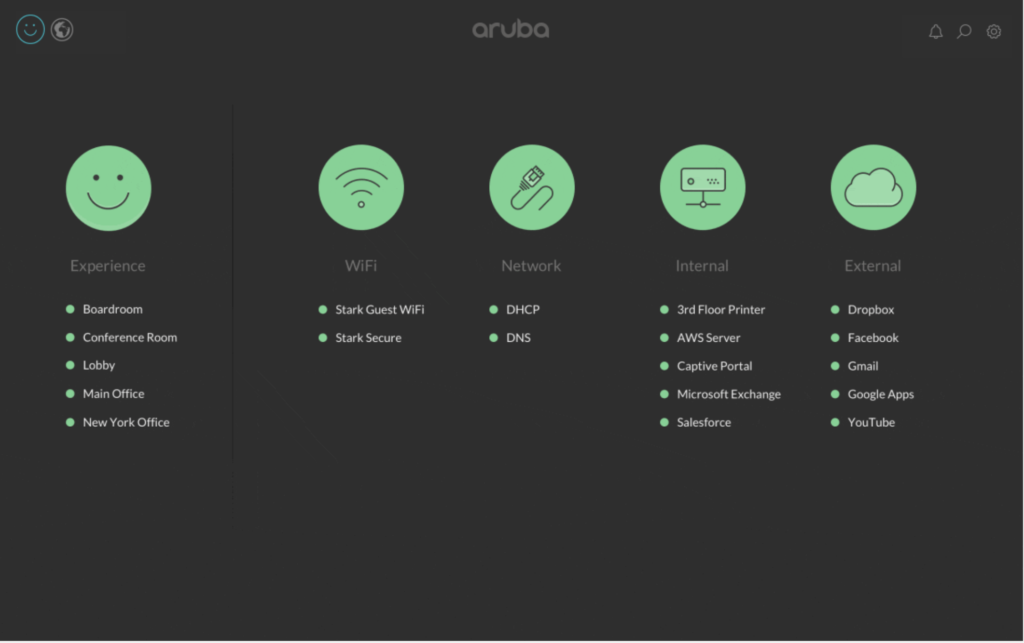 One way Aruba approaches this is via User Experience Insight dashboards. Instead of relying on failure and tickets, the Insight sensors are continuously monitoring. Through the monitoring system, tickets can be raised automatically through the dashboard, notifying users of potential problems before they become bigger issues. This helps create piece of mind and eliminates the need for those quick fixes.
One way Aruba approaches this is via User Experience Insight dashboards. Instead of relying on failure and tickets, the Insight sensors are continuously monitoring. Through the monitoring system, tickets can be raised automatically through the dashboard, notifying users of potential problems before they become bigger issues. This helps create piece of mind and eliminates the need for those quick fixes.
A Trusted Environment that Just Works
Creating an environment that is resilient, reliable and something employees can trust to just work for their requirements is one step closer to maintaining the relationship with technology and people. This can ultimately make a major (and positive) impact on one of your cybersecurity program’s greatest downfalls — user acceptance.




