
Recently, I was discussing some complex security subject of the impact of IT security and vulnerabilities on people within an organization and my friend Rob Markovic (@vRobM) commented, “Humans have no firewalls,” which was such a salient point that it brings us to our very discussion today.
Humans Have No Firewalls
I’m sure you’ve heard it said before that the greatest asset to an organization is its people. In the same breath, the most vulnerable part of an organization is its people. These factors drive businesses to provide comprehensive security training for all staff on what things to watch out for in the manner of social engineering, etiquette and so forth. I’m sure all of you reading this can recall your monthly, quarterly and yearly training that provides such depth in what to watch for and how to stay ahead of any security threats on the horizon. Right? Everyone does that, I’m sure of it? Nobody? Okay, you in the back, ONE of you probably has that. I’m kidding, really. The truth is, it is pretty rare that organizations do that unless they are explicitly regulated to conduct comprehensive trainings, and even then, it is often just to check the box.
Even if we are trained on what to watch for, it’s really not left up to the individual to pretty much ‘figure it out’ on the job. How far do you go with your diligence? You see someone trying to follow you into the building (tailgating), so you stop them and ask to see their badge if you don’t recognize them. If they show you, you did your part, and let them in. Or you might make them explicitly badge themselves in, and if the badge opens the door you even went above and beyond and did your part. If your job is not in physical security enforcement, you’ve done everything you’re expected to do. Whether that person was nefarious, using a cloned badge, or they were a legitimate employee yet considered an insider threat (such as those people who secretly steal information from the business), what can you possibly do at that point? You can diligently do your best to “see something, say something” and keep a good security posture in general.
Phishing is Old But New Again
You may remember hearing about phishing for the first time back when your grandfather told you about it: “People would send us emails with links we weren’t supposed to click!”
We thought phishing was a thing of the past, a problem long gone in an ancient era. It certainly shouldn’t be a daily problem in 2020. Yet, it is. Phishing emails trying to get you to open attachments that may be ripe with malware or ransomware. Phishing emails that ask you to do something like send all of the company W-2s to an email that you think is an internal person, but instead goes outside the organization. Or the very common phishing email that tells you something is bad (account is locked, you have money waiting for you, a password has expired, your credit card has been compromised), yet instead of taking you to the legitimate domain, instead it takes you to a nefarious actor’s domain with the sole purpose of stealing your credentials.
IT Phishing Leads to Security Shaming
In many organizations, IT has gotten wise to the phishing tactics on the horizon and has been using various tools like Automated Phishing Campaigns to target and send messages to their internal staff as a means of educating them on phishing campaigns. This is to help see who might be more likely to click a bad link so they can learn from their mistakes. Unfortunately, the sad reality of this, is this has led to Security Shaming, as the campaigns IT puts together have gotten more sophisticated, just as the bad actors’ campaigns have.
I’ve seen IT teams go so far as to reproduce their own internal IT systems in the form of phishing campaigns with identical or nearly identical links, to get the users to ‘click’ on these things, and when the users fail they shame the user or, even worse, give matters to HR for their permanent file with the possibility of it being a fireable offense.
What’s worse is you may get links and emails from domains that look PERFECTLY acceptable to the naked eye, yet instead the domain is registered with the “a” or “e” replaced with the Cyrillic letters “e” and “a”. This is called an “IDN Homograph Attack” and is a great read if this is the first time you’re hearing about it! You can even play along at home using this Homoglyph Attack Generator just to see how terrifying something like a simple listed ‘link’ can look.
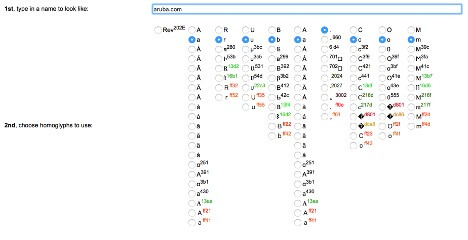
You might be asking, “What can I possibly do if the domain LOOKS appropriate in the link?” The honest to goodness truth is, even if you ‘trust’ the link, it might just make sense to hand-type the domain in, especially if this applies to something that matters to you, like your banking, retirement or personal accounts in general. It’s easier and better to be safe than sorry, and as you can see, this is something *very* easy to potentially exploit, in the form of email or otherwise.
If you’re an end user you should embrace that you have no firewall, and do your best to notice what you can, and try to act appropriately, and if something matters to you, don’t trust by default. If you’re a security admin or network admin, try not to shame your users, as they’re doing their best. Lean in favor of solutions that can help them not be able to make mistakes like access policy enforcement with Aruba ClearPass or other functional network access control capabilities or the Aruba SD-Branch solution. If it’s impossible for your end users to make a mistake, then there are no worries about them making them!
No matter what solutions, strategy or approach you adopt, keep working hard at it, because security is not something that happens quarterly, nor only when you’re in the office. Stay safe out there, watch what you click, and frankly don’t even click if you don’t have to.
Good luck!




