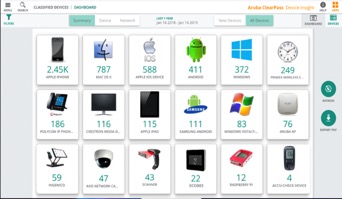
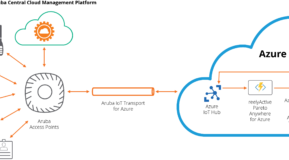
It was only a year ago that I expressed concern over the inevitable security apocalypse. I didn’t intend it to be foreshadowing or forecasting the pains, the woes and the concerns that we face today. What we have learned in this short time is that the pains are being felt in areas that are a little different and some unexpected.
Bring-your-own-device (BYOD) and the Internet of Things (IoT) have been seen as the major threats on the horizon and concerns that could bring about risk and compromise to many an organization. However, these concerns were often cast in the light of the insider threat – someone bringing in a device and having it infect or cause pain throughout the organization.
The Remote of My Remote is My Enemy
Looking back only as far as a few months ago, most IT managers and directors were not thinking about how to absorb the logins of hundreds, thousands, or even the better part of their entire staff connecting in from a remote location, let alone that location being their homes.
People have had to connect over VPN for secure connectivity, and many IT resources needed to be expended to help them. Aruba’s remote access points and secure VPN clients have helped to ease the transition of remote users and has dramatically simplified work from home experiences. However, let’s look at video conferencing tools, for instance. We can already identify multiple challenges – from the number of organizations going from a trial of video conferencing applications to a production roll-out within days – with little to no preparation time. Imagine the amount of productivity lost when half of the attendees suddenly realize that they can personalize and change their virtual background, and focuses on this!
It’s All Fun and Games, but WAIT, SECURITY?
While everyone has been rushing to establish connectivity, an unfortunate many of them have completely forgotten about enforcing the same kind of security standards that they’re expected to fulfill internally, but at the edge and at the remote user. And this is not merely limited to attackers stealing Windows credentials via Zoom (or MacOS, or compromising host).
We still have all of the same challenges we would normally face within our walls. Now those challenges are spread to the homes of all of our users, including those people who practice good device and network hygiene and many others who may have no idea what any of these words mean. Fortunately, there can be ways to get some device insight into the community and the user space so you can focus on service delivery and not trying to figure out who is connected on your network, whether they should be authorized and the various devices and sub-devices that may be in play have any right to be connected.
When all these virus concerns settle down and things go back "to normal," the network may return to look like it had mere months ago, or it may be permanently changed forever. It's the decisions we make which can help ensure that our network of tomorrow will be more versatile and able to respond to the next challenges we may face, be it a remote network overload, excessive VPN connections, application threats that live remotely on all of our devices, or even security visibility challenges whether wired, wireless, remote or beyond.
Thinking proactively, the coming months will be overwhelmingly important for IT admins, network admins, sys admins and the like to scour their networks to ensure unknown challenges and new concerns have not slipped in during the mad-rush to "remote-ify" all of the end users. This may be the silent threat ready to infect or already infecting our networks that may need to be dealt with.
Stay safe, practice good network and personal hygiene and we will all band together to get through this.