
WAN edge infrastructure is one of the most rapidly changing areas of IT, driven largely by the unabated migration of business applications to SaaS offerings and to public clouds or IaaS instances. As reported by Forbes, 83 percent of enterprise workloads will be hosted in the cloud by 2020. No longer centrally hosted solely in corporate data centers, applications are now hosted anywhere, and often in multiple locations.
SaaS and IaaS providers strategically host their services in multiple data centers around the globe in metropolitan cities where business users are located. Connecting users to the closest SaaS and IaaS instances minimizes data transmission latency or delay and delivers the highest cloud application performance to end users.
A Modern Cloud-first WAN Architecture
However, traditional device-centric WAN architectures based on branch routers can’t take advantage of the distributed nature of cloud applications and services. Why? Because they typically route cloud-destined application traffic from the branch back to a headquarters-based security stack before sending it to the internet to protect the enterprise from threats. Traffic is then steered to SaaS or IaaS instances closest to HQ rather than to instances closest to users in the branch. This “trombone” traffic pattern adds latency which negatively impairs performance.
The solution is local internet breakout (LIB) – sending cloud-destined traffic directly from the branch to the closest SaaS or IaaS instance and doing so over the internet. LIB requires a level of application awareness and automation not available with traditional routers and has spawned a new, modern, software-defined approach to the WAN – SD-WAN.
A New Security Approach Complements a Modern WAN
But sending traffic over the internet is not as secure as private leased line connections. Actively using internet connections to transport enterprise application traffic increases the attack surface and exposure the enterprise to vulnerabilities. Therefore, just like with the WAN, delivering the best cloud application user experience requires a new, modern approach to security. This modern approach is cloud-hosted security.
Cloud-hosted security services centralize the entire security stack and locate it in the cloud instead of on-premise using dedicated, expensive security appliances at each branch location. The cloud-hosted security stack not only includes next-generation firewall services but also IDS/IPS, URL filtering, UTM, antivirus protection, sandboxing and more. Automated daily threat definition updates ensure consistent security policy enforcement across the enterprise.
Cloud-hosted security services utilize security enforcement points of presence (PoPs) strategically located – and even co-located – near SaaS and IaaS PoPs. By locating security enforcement as closely as possible to branch locations and to SaaS and IaaS instances, it enables local internet breakout to deliver the best application performance and branch security.
Automating Cloud-hosted Security Service Chaining
This is where the complementary nature of SD-WAN and cloud-hosted security is really on point. The SD-WAN must identify application traffic and steer it appropriately to enforce granular security policies. An enterprise might define the following policies:
- Backhaul traffic bound for data center-hosted applications back to headquarters
- Send trusted, whitelisted applications traffic like unified communications-as-a-service or Office 365 directly to their provider’s data center
- Send all other internet-destined traffic to the closest cloud security enforcement PoP
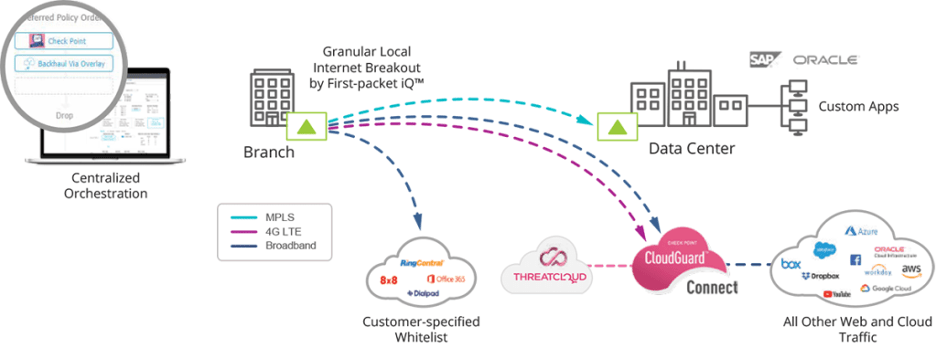
Implementing policy #3 requires establishing secure IPsec tunnels between the branch SD-WAN appliance and the closest cloud-security enforcement PoP. Manually configuring these tunnels for 10s, 100s or 1,000s of branch locations is complex, time-consuming and error prone.
Thankfully for IT, Aruba and Check Point have partnered to automate and streamline cloud-hosted security service chaining. From the Aruba Orchestrator management console, a user provides their Check Point subscription information. With a few mouse clicks, a fully automated process configures hundreds or even thousands of tunnels between branch locations and Check Point CloudGuard Connect enforcement PoPs in just minutes instead of hours or days. Not only reducing the time to deploy, centralized orchestration minimizes the potential for human errors and provides more consistent security policy enforcement across the enterprise.
For enterprises that require on-premise security for data privacy or compliance requirements, Aruba automates service chaining to the CloudGuard Edge virtual security gateway. CloudGuard Edge software can run on existing office IT equipment including universal customer premises equipment devices.
Even when adopting a cloud-hosted security architecture, the branch still needs a basic stateful zone-based firewall to detect and protect against incoming threats. The Aruba EdgeConnect SD-WAN platform unifies zone-based firewall functionality in the platform software, eliminating the need to deploy purpose-built security appliances at the branch.
The highly complementary Aruba and Check Point integration provides a secure, high-performance modern WAN edge architecture that
- Delivers the highest quality of experience for users and IT
- Increases business agility by accelerating security deployments
- Improves enterprise security policy enforcement
- Lowers IT resource costs
Silver Peak was acquired by Aruba, a Hewlett Packard Enterprise Company.




