 As a user of both open and Pre-Shared Key (PSK) wireless networks, I understand that my data is at risk of being intercepted. We all know that anyone running a capture can see the 1s and 0s running over the air, but shouldn’t our users have an expectation of privacy? Is it reasonable to expect our users to mitigate the risk of an eavesdropper themselves, or should the infrastructure we support minimize the attack surface?
As a user of both open and Pre-Shared Key (PSK) wireless networks, I understand that my data is at risk of being intercepted. We all know that anyone running a capture can see the 1s and 0s running over the air, but shouldn’t our users have an expectation of privacy? Is it reasonable to expect our users to mitigate the risk of an eavesdropper themselves, or should the infrastructure we support minimize the attack surface?
In June 2018, the Wi-Fi Alliance announced a new certification program for WPA3. This new standard includes requirements for Simultaneous Authentication of Equals (SAE) and Management Frame Protection (MFP). It also originally included discussions of Opportunistic Wireless Encryption (OWE); however, that protocol was broken out of WPA3 and is now a separate suite called Wi-Fi Certified Enhanced Open. The best part of WPA3 is that there is no need to rip and replace your existing hardware. To enable WPA3, all you need is a software update from your device manufacturer.
Secure Authentication
Simultaneous Authentication of Equals (SAE) is based on RFC 7664 – Dragonfly Key Exchange and has been used previously to secure mesh networks under 802.11s. SAE used in WPA3-PSK removes the existing WPA2-PSK vulnerability for offline dictionary attacks. In legacy PSK environments a password or passphrase is hashed by both the AP and the client. The hash is sent and compared and, if successful, the authentication is completed. An attacker can capture these frames and run them through a tool such as Aircrack-ng to run a dictionary attack and determine the PSK.
With SAE, the password and password-derived information is never sent over the air. This completely eliminates the threat of an attacker capturing the authentication sequence to attack using an offline method. The only avenue of attack is to actively attempt connecting to the network, which after a few attempts, should alert the administrator and block the attacking client.
Protection From Rogue Management Frames
Another change that will have a positive impact is the requirement for Management Frame Protection. MFP is negotiated between the client and the AP and prevents a device from being sent rogue management frames. MFP will not just protect users in WPA3, but also those connected to an open network supporting OWE.
Previously, when MFP was optional, users could be sent deauthentication frames by attackers, who could then capture authentication frames as the client reconnects to the network and crack the PSK using the dictionary attack mentioned earlier.
Another scenario we will see fixed using MFP is a DoS attack where an attacker sends continuous deauthentication packets to all client devices, preventing anyone from accessing the network.
Secure, Open Wi-Fi
In my opinion, the most important feature related to WPA3 is Opportunistic Wireless Encryption (OWE). OWE has been rebranded to Wi-Fi Certified Enhanced Open by the Wi-Fi Alliance and it is technically a separate part of the new protocols, not a core part of WPA3 itself. OWE is something that must be implemented on a vendor-by-vendor basis.
Why the Wi-Fi Alliance considered a technology that fixes the most fundamental issue with public wireless as an optional element is beyond me. Hopefully, vendors and manufacturers are able to see the need for OWE and implement the technology in their products.
OWE, as defined in RFC 8110, outlines a method for clients and access points to derive a pairwise secret key based on a Diffie-Hellman key exchange. Each client will get its own unique key per session, allowing for encrypted Wi-Fi without the user having to do anything more than click and connect.
In the background, OWE-enabled SSIDs will advertise two separate BSSIDs to allow for an encrypted OWE network and an unencrypted network for legacy clients to connect to. Broadcasts are sent out by both the open SSID and a hidden SSID. The open SSID will include a new information element called ‘OWE Transition Mode’ that advertises the OWE hidden SSID and BSSID.
OWE-capable clients will connect to the BSSID provided, derive a Pairwise Master Key (PMK) from an ephemeral private key and the AP’s public party key, and perform a four-way handshake to derive the traffic encryption keys from the PMK. This process is similar to what we see during a WPA2 four-way handshake, but there are no certificates or credentials provided by the user in SAE.
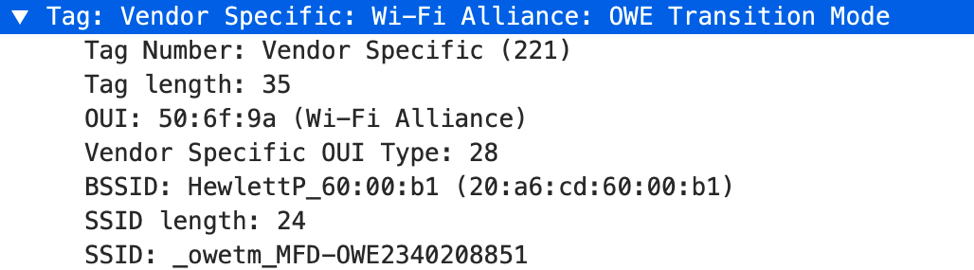
Again, it is important to note that OWE is not a core requirement of WPA3. Instead, it is up to the AP vendors to implement this optional enhancement. But, as you can see, OWE can greatly increase the security of open Wi-Fi networks.
For additional information on any of the content covered here I recommend listening to Dan Harkins’ interview on Aruba Unplugged - Episode 8: Demystifying WPA and the WPA3 Security Standard. Dan literally wrote or cowrotethe RFCs for many of the technologies used in WPA3, so it’s safe to say he knows what he’s talking about. Also, thanks to Rowell Dionicio and Tech Field Day for providing the packet captures in the example above. You can download the capture here to examine on your own.




