Blockchain with immutability, distributed consensus, established trust, distributed identity and eternal verifiable claims may sound like the ultimate security foolproof technology. But new age security attacks are emerging, which are very sophisticated and can cause huge irreparable damages. Understanding these attack vectors is very important for anyone developing and deploying blockchain solutions. Prevention is better than cure!
In this article, the emerging new age blockchain security attacks are grouped into four categories:
- Peer-to-peer network-based attacks
- Consensus & Ledger-based attacks
- Smart Contract-based attacks
- Wallet-based attacks
Peer-to-Peer Network-based Attacks
- Eclipse attack– A node will depend on “x” number of nodes selected using a Peer selection strategy to have its view of the distributed ledger. But if an attacker can manage to make the node to choose all the “x” number of nodes from his malicious nodes alone, then he can eclipse the original ledger’s view and present his own manipulated ledger to the node.
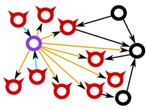
Source: http://cs-people.bu.edu/heilman/eclipse/
- Sybil attack– While the Eclipse attack is about eclipsing a user’s view of the true ledger, the Sybil attack targets the whole network. In a Sybil attack, an attacker will flood the network with large number of nodes with pseudonymous identity and try to influence the network. These nodes, though appearing like unrelated individuals, are operated by a single operator at the back. In this case the objective is not to target one user, but a number of nodes or network as whole, and generate a fork in the ledger if possible, allowing the attacker to make double spending and other attacks.
Consensus Mechanism and Mining-based Attacks
- Selfish mining attack: Many blockchains consider the longest chain to be the true latest version of the ledger. So a selfish miner can try to keep building blocks in stealth mode on top of the existing chain, and when he can build a lead of greater than two or more blocks than the current chain in the network, he can publish his private fork, which will be accepted as a new truth as it is the longest chain. He can do transactions in the public network just before publishing his longer stealth chain to reverse the transaction he just did. This effectively provides a small window for the attacker to do double spending based on this ability to build a stealth chain by building sufficient block lead (Finney attack).
- Mining malware: Malware uses the computing power of unsuspecting victims’ computer to mine cryptocurrencies for hackers. China reported that over a million computers were infected by this malware and helped attackers mine more than 26 million tokens of various cryptocurrencies.
- 51% attack: This attack is possible when a miner or a group of miners controls 51% or more of the mining power of the blockchain network. Though it is very difficult to happen for large networks, the possibility of a 51% attack is higher in small networks. Once a group has majority control over transactions on a blockchain network, it can prevent specific transaction or even reverse older transactions.
- Timejack attack: Nodes in certain blockchain networks like Bitcoin depend on internal timing derived from median time reported by its peer nodes. For example, you depend on your friends to know the time. Let us say an attacker manages to put a lot of malicious people in your friends’ list, then he can manipulate your time. The first step to this attack can be an Eclipse attack on the target node. Once this attack is complete on a target node, then the target node will not accept blocks from the actual network as the timestamp of the blocks will not be in line with its timestamp. This provides an opportunity for the attacker to be double spending or do transactions with the targeted node as these transactions can’t be submitted to the actual blockchain network.
- Finney attack: If you can mine a block with one of your transactions in it and keep it in stealth, there is an opportunity for you to double spend the money. If a merchant accepts the unconfirmed transaction, you can transfer him this earlier transacted currency. Next you publish the earlier mined block, which was kept in stealth, before your new transaction is confirmed on network.
- Race attack: This attack is minor variation of the Finney attack. The difference is that the attacker need not pre-mine the block with his transaction, which he intends to double spend. During the attack, the attacker submits an unconfirmed transaction to a merchant (victim) and simultaneously does another transaction which he broadcasts to the network. It is easier for the attacker to launch the attack if he is directly connected to the merchant’s node. This would give the merchant an illusion that his transaction is the first, but that is never submitted to the blockchain network by the attacker.
Smart Contract-based Attacks
Smart contracts are completely automated contracts, which execute transactions in an agreed upon way between participants, with inputs from the real world and without intervention from any middlemen. So once started, a smart contract cannot be stopped. The transaction once completed and written into blockchain becomes immutable. This gives a guarantee to participants of returns based on their performance, as agreed upon while entering the contract. But think what would happen if the Smart Contract has bugs: Millions of dollars are in stake and no one can change it. We are going to look at such attacks or attack vectors relating to smart contracts.
- The DAO attack: The biggest exploitation in the history of cryptocurrencies is the “THE DAO” hack. Decentralized Autonomous Organization was an ambitious feature of Ethereum. A company called Slock started crowdfunding for a project called “The DAO”. The crowdfunding got an overwhelming response, collecting 12.7 million Ether, valued at $150 million then ($2 billion today). But an attacker identified a vulnerability in the code where by a recursive withdraw function could be executed without checking the settlement of the current transaction. So the attacker started the attack by contributing a small amount and requesting withdrawal with a recursive function. This allowed him to pull out almost $70 million dollars out of the crowdfund.After this the events took an interesting turn. The Ethereum Foundation threatened the attacker to stop the attack and freeze the account. The attacker responded saying that he was playing as per the agreed upon contract and an intervention through a soft or hard fork will be a breach of contract, which he can take to court (Read the Attacker’s open letter.) But he stopped the attack. Later the Ethereum Foundation went with a hard fork to recover the money, though this decision raised many concerns of autonomy of smart contracts. This hard folk resulted in two Ethereum currencies – Ethereum & Ethereum classic and a lot of controversy.
Wallet-based Attack
- Parity Multisig Wallet Attack: This was the case of a vulnerability with the parity client wallet hacked by an attacker resulting in holding up of 500,000 Ether ($77 million today). Wallet contracts are additional logic than can be built on user wallets for regular automated payments. To reduce the gas or transaction fees, the parity Multisig wallet functionality (Multisig wallet is like a joint account in bank with multiple owners) used a centralized Library contract. But they left some critical functions open, resulting in a vulnerability, which was exploited by the attacker. The attacker added his account as owner in the library contract, so for all wallets implemented after a particular date, the attacker became a joint owner. Then he triggered a kill function, which froze the currencies in the wallet. He basically locked $155 million as of that day, forever in cryptographically inaccessible wallets.
Conclusion
Mistakes in blockchain deployment can be very costly, especially in permissionless networks, as anyone can participate, their identity are anonymous and reverting back mistakes is impossible. The majority of the attack vectors and vulnerabilities discussed in this article have solution when found before deployment. But considering the immutable nature of blockchain and hard fork or soft fork not being a practical option, through understanding of concepts, security audits and detailed testing are very important before deployment.
Read More on Blockchain
Enterprise Standards Blockchain Collaboration
Tools for Developing Real-World Enterprise Blockchain Applications
Blockchain: Do You Have an Identity Problem?
GDPR: Control Over My Personal Data, My Right




