Many network administrators that have implemented WPA2-Enterprise get asked: can you fix the issue that I need to accept a certificate on first connect?
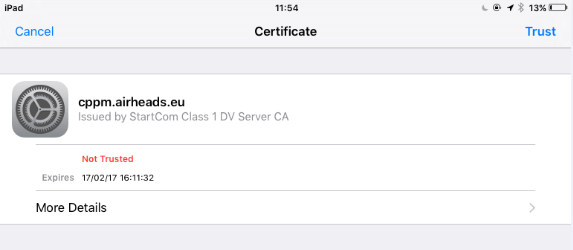
That is the million dollar question... why do we need to accept the certificate the first time on a wireless connection? And why is Facebook's certificate always accepted and trusted without any user prompt?
To explain everything, let me start with the Facebook case which boils down to HTTPS. An increasing number of websites on the internet have started to use HTTPS, which adopts the same certificates that we use for Wireless LAN. Because of those HTTPS connections, you can be sure that you connect to Facebook, and that no one in between has tampered or impersonated that connection. To ensure your connection is secure between you and Facebook, the Facebook web server presents a server certificate. That certificate is automatically validated by your web browser, and only if it the connection is really Facebook.com, is the site is displayed on your screen. You can see a successful validation by the Green lock or Green URL bar in your browser. If there is something wrong with the connection, a security warning is displayed to the user. This is a somewhat simplified story of what is happening in the background, and you should be able to find a lot of information on the web how this works exactly (for that check: ClearPass Certificates 101 Technote - Appendix B; or WikiPedia TLS Handshake).
For a website, like Facebook, the automatic validation works because your browser can check that the URL (www.facebook.com) corresponds to the Common Name (CN) or Subject Alternative Name (SAN) fields which are included in the presented server certificate. So we have a direct link between the DNS name of the website and information in the certificate. And your web browser can trust the website at first sight without additional prior knowledge.
So why can't this work for my Wi-Fi? The short answer is because the identifier for Wi-Fi is an SSID (Network name) which is not central registered. The domain names, like facebook.com, are registered and linked to a trusted owner. You can pick any SSID that you like, and configure it. If you want to name your wireless network Aruba, Facebook, or eduroam, you can. There are even funny SSID Name generators out there, that give you names like: "Mum use this one", "Searching...", "Federal Bureau of Investigation" or "Pretty fly for a WiFi". The fact is, there is no system to make SSIDs unique and bound to an organisation. This also means that when you connect to your corporate SSID, there is no method to validate if you are connecting to the official corporate network, or to someone else's network pretending or deliberately spoofing the corporate network.
Wireless clients respond differently to this validation dilemma. Most Android devices silently assume that the first time you connect to a WPA2-Enterprise network the certificate you see is the right one. Windows 10 asks you if you expect this network at this place, and then stores the certificate. Windows 7 and Apple IOS devices show the certificate for the network and ask the user if this is the correct certificate for the network you want to connect to. An initial validation must be done to make sure you are connecting to the legitimate network and the authentication server.
So how can prevent the certificate question popping up? Well, I hate to be the bearer of bad news but the thing is, you can't unless you pro-actively configure a device what certificates to trust for the corporate network. These popups come with a reason. Unfortunately, not so many people understand what they mean. That means that you as network administrators should help your users by:
- For Windows corporate clients, you can use Active Directory Group Policies to enrol your clients with the WLAN profile including which certificates to trust.
- For Managed mobile devices, you use your favourite Mobile Device Management (MDM) or Enterprise Mobility Management (EMM) system, you can usually use that to do the same with your managed mobile devices.
- On unmanaged devices, you should pick a solution like ClearPass Onboard or QuickConnect to get the settings pushed out and configured.
If you don't tell a device in advance what authentication certificate to expect and trust, it cannot be sure that it connected to the authentic corporate network. And connecting to rogue networks or rogue authentication servers imposes huge security risks, which your device is explicitly warning you for or preventing to, by those hated security popups. Remember, those popups come in peace, and while there is no such thing as the trust at first sight in WPA2, you should help your end users by giving them the trust before they need it.
So what security topics give you headaches? Or security questions you did not dare to ask because they might appear to be stupid? Please let me know, so I can write another blog on that topic. Oh yeah, for the second category of questions, you may send me an Airheads private message.




