Why UEBA and why do I need it?
As expected, this year's show in San Francisco provided the opportunity to catch up with old friends, meet a few new ones, see what solutions were being touted as the next big thing, and hear from non-vendors on why they needed something else. Since nearly every booth was talking about analytics of some flavor, I can see why the fog needs to be lifted a little.
Because of our recent acquisition of Niara, that is in the Behavior Analytics space, we were getting our fair share of questions. It reminded me of the shows where the theme was deep packet inspection or network access control. The questions weren't about how the new technology could help, but more about why their existing tools needed to be replaced.
For NAC, I remember repeatedly explaining that an active directory (AD) wasn't really built to provide data on where a network connection was being established or when. And, why asking IT to enter information about every BYO device into an AD wouldn't scale. It took some time for the questions to die down, so I expect the same will happen now.
So, while not a comprehensive list, let's take a look at what I did hear:
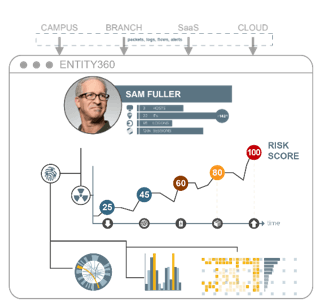
- For one, lots of questions on what UEBA stood for. It's an acronym--User and Entity Behavior Analytics. And it's not pronounced You-eee-Bah, it's just U-E-B-A. The idea is that in today's mobile workplace where users carry multiple devices, connect from everywhere, at all hours, it's beneficial to baseline connection and usage patterns per user, while inside the network. The same is true for entities like cameras, an Amazon Echo and other great new devices that may make it into your engineering labs, production networks or executive briefing centers. I should probably mention that securing IoT was something else that was big at RSA this year.
- What benefit does UEBA provide? Let's say that a user's smartphone and laptop are both connected at the same time but in different offices, in cities that are hours apart. UEBA is a way to capture that incident and determine if it's normal behavior. Maybe the user shared a device, or their password, or one of the devices was stolen. It could be something as simple as they left the laptop in the office while traveling, but how would IT know without a baseline. In the above scenario, the user could be automatically contacted to determine why their risk score shot through the roof. What if one of the devices was downloading terabytes of data when normal behavior was megabytes, the offending device could even be disconnected from the network. All that would be needed was integration from the UEBA solution with a policy management solution, like Aruba ClearPass for the enforcement component.
- The next question was, why UEBA versus a SIEM? This was probably the most perplexing to people due to our inherent relationship with the HPE team that offers a SIEM. Where UEBA differs is in its ability to use machine learning (behavioral) models instead of known signatures to identify possible attacks. In fact, our UEBA solution works with all major SIEM solutions like ArcSight, QRadar, Splunk and McAfee ESM. Again, a UEBA solution is intended to provide focused visibility into how users and entities are utilizing internal infrastructure and resources. As another point of contrast, UEBA is not a traditional log aggregation solution which is why SIEMs still have a prominent role in the security ecosystem.
While there were definitely more questions, I'll have to save it for a future blog where we can cover machine learning more, and go a deeper on why integration with a policy management solution makes sense. If you have questions of your own make sure to let me know.




