In multi-vendor environments successful interoperation is a major concern for customers. It is vital that products work together, the Networking equivalent of 'Everyone play nicely together' for the good of all. Happily, this blog details one such case of harmonious living, namely between Aruba ClearPass and Cisco Prime.
When using Cisco Prime you have the option to configure authentication to a remote AAA server via RADIUS or TACACS+. I configured Cisco Prime to use Aruba ClearPass as remote AAA server based on the TACACS+ protocol. The configuration of an AAA server in Cisco Prime is very straightforward.
Configure the AAA Mode Setting under Administration / Users / Users, Role & AAA / AAA Mode Settings to enable TACACS+ authentication.
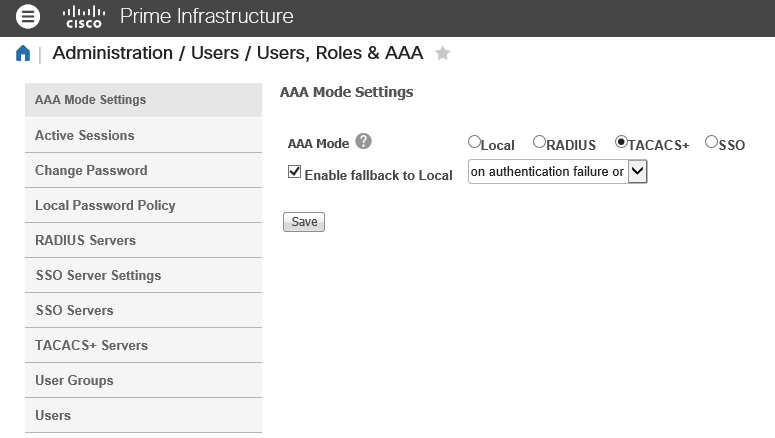
The next step involves adding Aruba ClearPass as TACACS+ servers via the option menu Administration / Users / Users, Role & AAA / TACACS+ Servers.
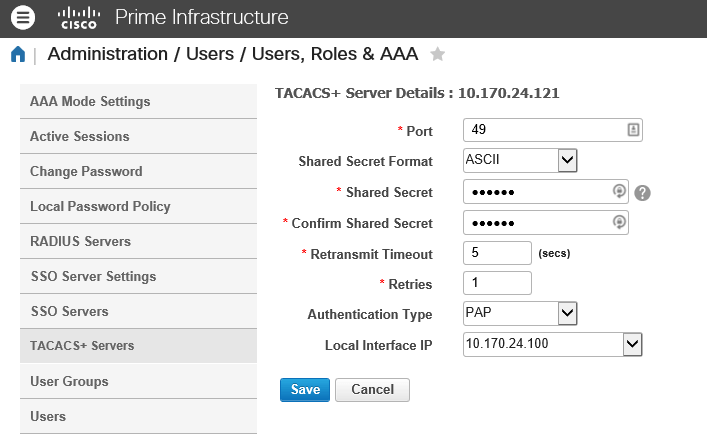
Of course, you to add the Cisco Prime appliance as NAD device to your ClearPass configuration, so Prime and ClearPass are able to communicate via TACACS+. I configured a TACACS+ service in ClearPass, which uses Active Directory as Authentication source and a Role Mapping to map the "Prime Administrator" AD Security Group to the role [Cisco Prime] At first I configured a simple TACACS+ Enforcement Profile. I used the same Enforcement Profile, which I also use to enforce privilege level 15 to switches and routers.
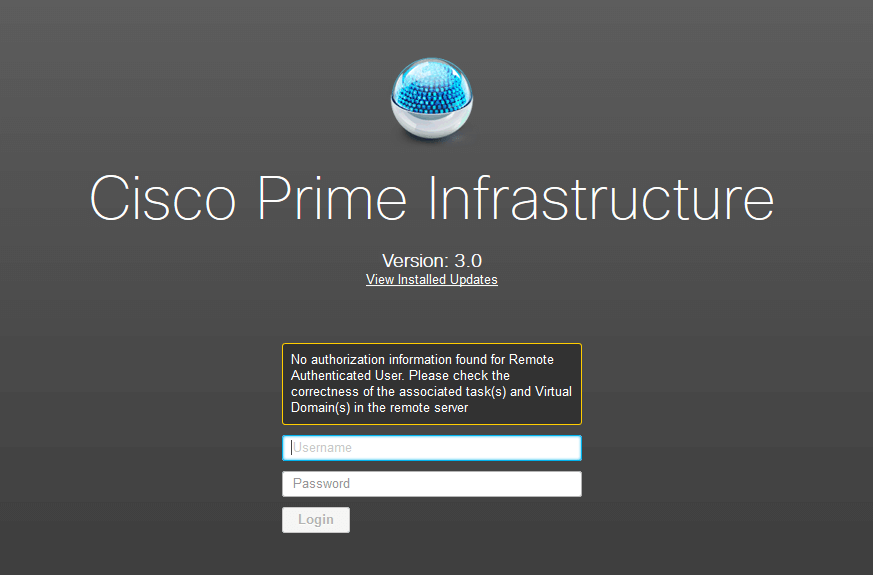
Authentication will fail at this point. In the Access Tracker I get the following error message: Tacacs service=NCS:HTTP not enabled. The login screen from Cisco Prime shows the following error message.
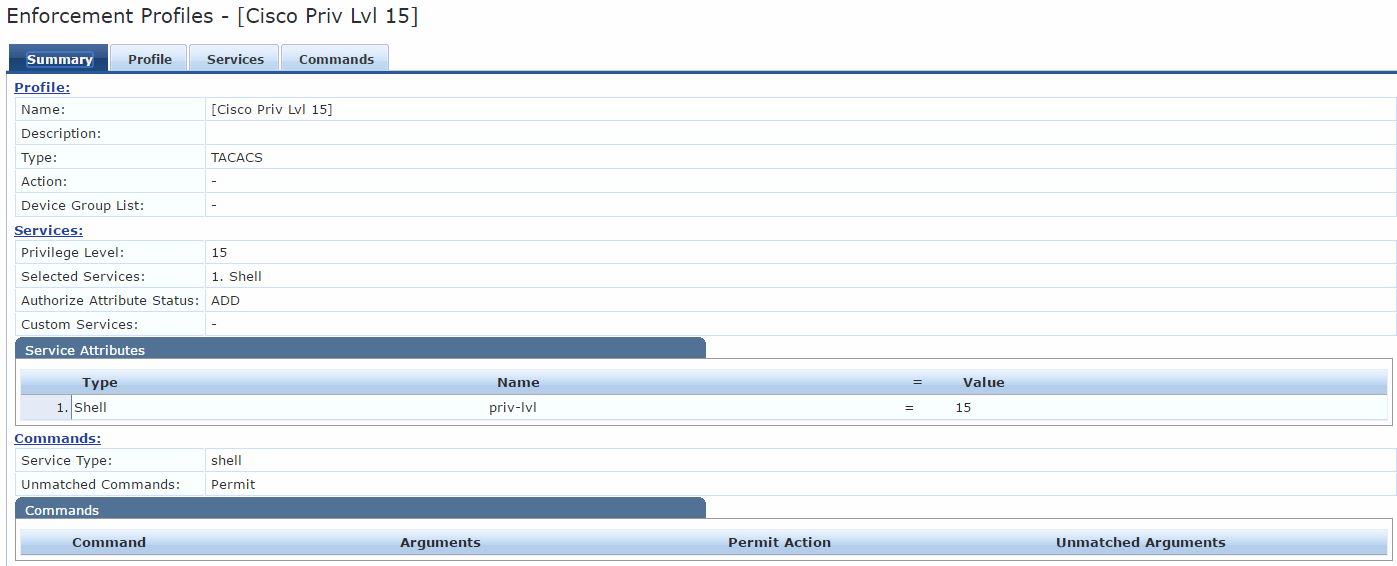
I created a new Enforcement Profile and selected the TACACS+ Services NCS:HTTP. Now I see an access granted in the Access Tracker, but I still get the same error message on the Cisco Prime website. After some digging in Cisco Prime I noticed that Cisco Prime needs to receive TACACS+ attributes from the AAA server to grant access and assign privileges and tasks to the user.
First you need to get the TACACS+ attributes from the Virtual Domain configuration. In the menu options navigate to Administration Users Virtual Domains. At the upper right corner, you have the option to "Export Custom Attributes".
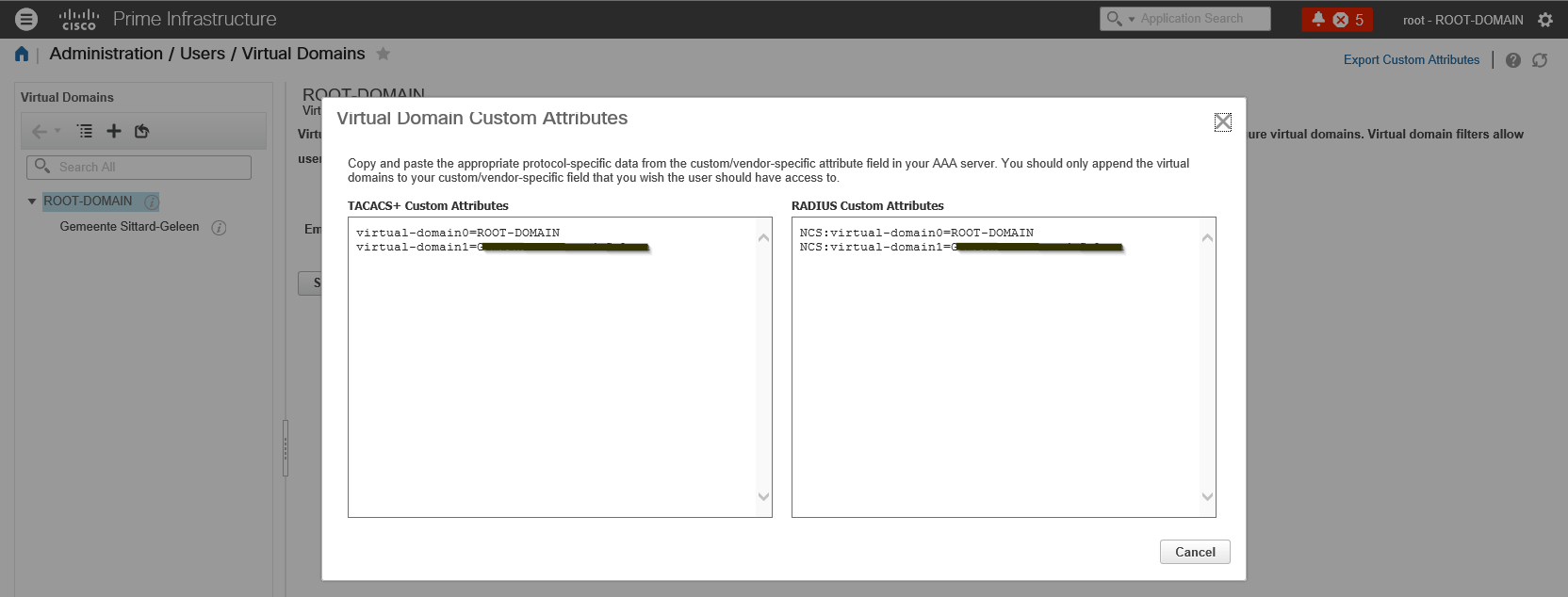
These attributes need to be configured in ClearPass.
As you notice you also need to configure these attributes if you would like to use RADIUS as the authentication protocol.
You also need to add the attributes from the user group. Navigate to Administration / Users / Users, Role & AAA / User Groups. Click the "Task List" option next to the User Group you would like to use. I use Root in this example.
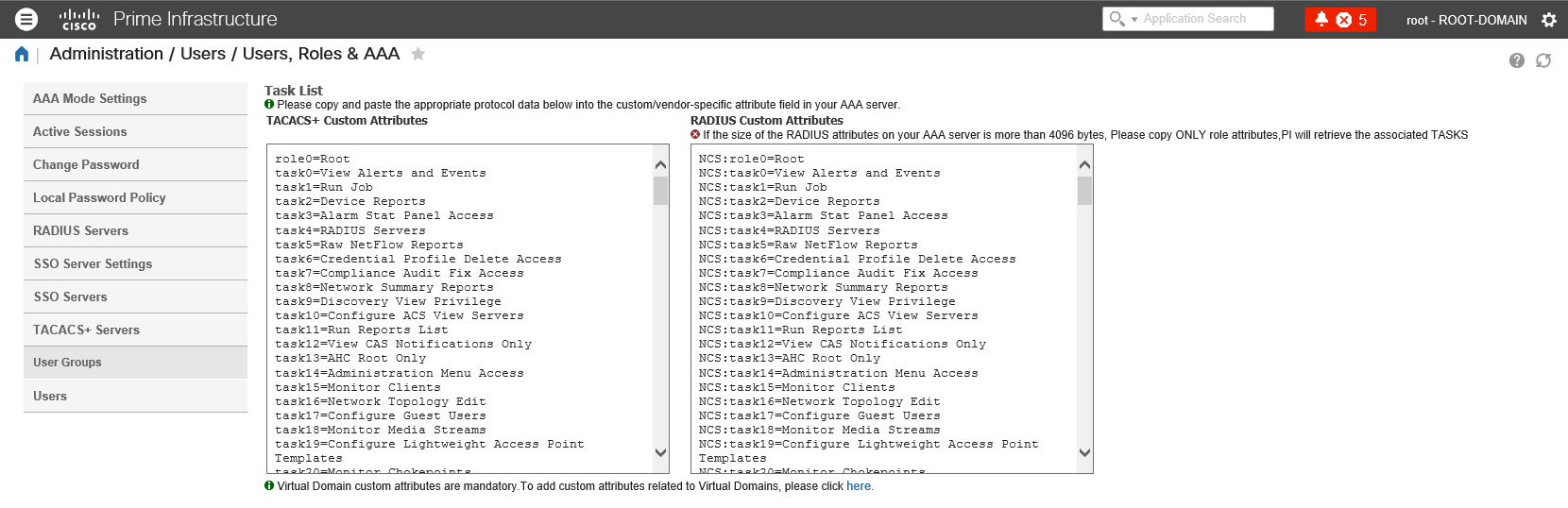
The User Group Root contains 194 tasks, which need to be added to the Enforcement Profile in ClearPass. Below you see a snippet from the Enforcement Profile configuration.
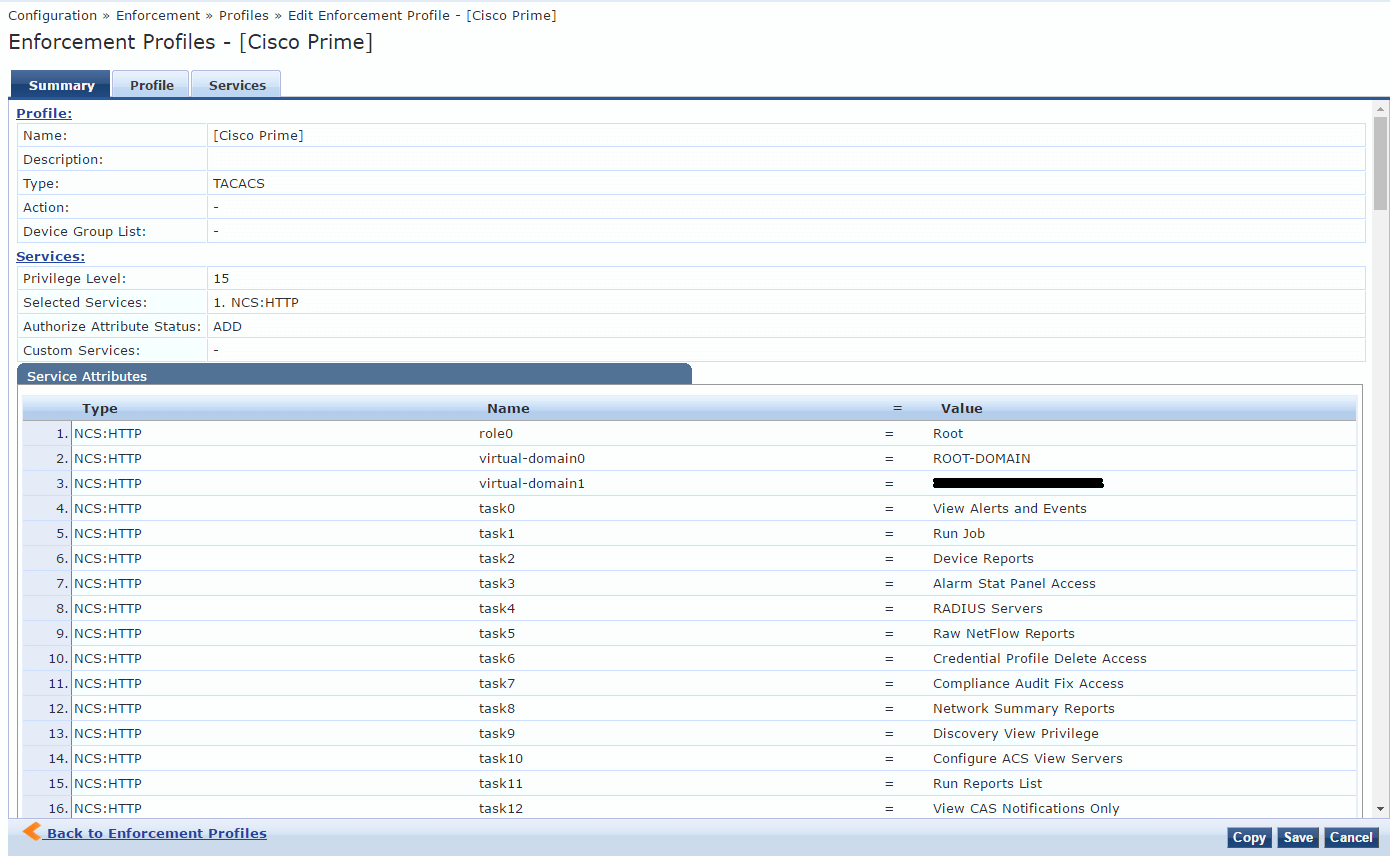
Adding all the attributes to the Enforcement Profiles assigns the correct authorization for your administrator users in Cisco Prime.
To make it easy, I exported the Enforcement Profile including all the 194 tasks for the Root User Group. You can download the Enforcement Profile in PDF format below. Just save the profile as XML and import the profile into ClearPass and you are good to go!!!




