
This is the third blog in a series that explores the changing role of the edge network as businesses transform their products and services. Learn the six new challenges that mobile, cloud and IoT created for edge switches. People primarily access the network through Wi-Fi, and that’s causing IT to rethink the role and importance of the edge switch.
Today, people use their personal phones and tablets at work without a second thought. But a few years ago, BYOD was a huge headache for the IT department. IT was in no position to tell the CEO that she couldn’t use her brand-new iPhone on the corporate network. It didn’t matter that the phone wasn’t on the approved devices list. Or that business information was mixed with personal photos. Or that the CEO’s kids loved playing Plants vs. Zombies.
Then it wasn’t just the CEO. Everyone wanted to use their personal phones and tablets at work. Mobile device management software was invented. Network access control, with 802.1X authentication, which was already used for corporate-owned mobile devices, was adopted. Software like Aruba ClearPass could identify a personal mobile device and place it in the right network based on the context and the user’s role. IT solved the BYOD problem and moved on.
The next wave of unknown, untrusted devices
IoT is the BYOD of the wired network. Like BYOD, IT administrators don’t know where these IoT devices are coming from and they have read enough news headlines not to trust them. They’re not necessarily in control, either. It might be the facilities or maintenance department who are driving IoT initiatives, and IT is lucky if these groups remember to talk to them before deployment instead of during or after.
IoT device security is a major challenge. Many IoT devices don’t support 802.1X authentication or client-based security. Manufacturers are retrofitting their existing “things” to be smart, often with low-security open source connectivity tools. These devices were never designed to be connected to a network and their makers aren’t necessarily security experts.
In other words, IoT has the same problem statement as BYOD: unknown, untrusted devices must be granted access to the corporate network. The difference is the huge variety of device types, typically without 802.1X support. A further difference is in the specialization of these devices, in that they only need to talk to one or even a few specific resources. Connected sprinklers only need to talk to the irrigation software in the cloud. Surveillance cameras stream to the local video recording server. A badge reader needs access to the building management system and Active Directory to check the latest policy for an employee before unlocking the door. Segmentation is therefore an absolute requirement for any IoT security solution.
Solving the IoT access problem
As an industry, we can take what we’ve learned from BYOD and apply it to IoT: network access control and network segmentation. Quite simply, IoT is the BYOD of wired networks.
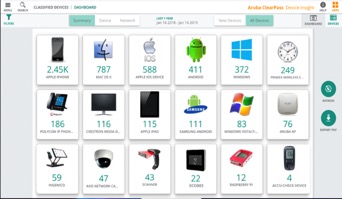 Organizations embarking on IoT can use Aruba ClearPass to identify a device, using 802.1X, MAC-AUTH or device profiling. Aruba’s new ClearPass Device Insight uses the power of the cloud and AI to discover and profile every device on the network, user or IoT, wired or wireless. Device Insight eliminates those blind spots into IoT devices and provides detailed identification.
Organizations embarking on IoT can use Aruba ClearPass to identify a device, using 802.1X, MAC-AUTH or device profiling. Aruba’s new ClearPass Device Insight uses the power of the cloud and AI to discover and profile every device on the network, user or IoT, wired or wireless. Device Insight eliminates those blind spots into IoT devices and provides detailed identification.
Once ClearPass places a device into its proper role, the switches dynamically apply the appropriate role-based policy. Policies can be enforced the traditional way, with VLANs and ACLs, or via the mobility controller, which has a built-in firewall and deep-packet-inspection (DPI) engine, so the traffic can be inspected and firewalled before it continues on.
With a robust way to ensure secure network access to IoT devices, IT managers can say “yes” to maintenance, security and other operational teams, just as they learned to say “yes” to CEOs with their holiday gift iPads a decade ago.
Learn More About the Changing Role of the Edge Network
Build Everything at Cloud Scale
Wireless Failure Domains and Bottlenecks…on the Wire




